You have no items in your shopping cart.
Advanced EIGRP Configuration for Reliable and Fast Networks
Efficiency, reliability, and scalability are crucial in today's network technology. This article provides a comprehensive overview of the Enhanced Interior Gateway Routing Protocol (EIGRP), a fundamental component of modern networking. This guide will cover the foundational principles of EIGRP and explore advanced configuration techniques.
EIGRP is a routing protocol that offers fast, reliable, and flexible network performance, designed to tackle the challenge of efficiently routing data across diverse and dynamic digital landscapes. It expedites network convergence, optimizes bandwidth usage, and enables intelligent path selection. It offers a suite of benefits, including efficient path calculation, enhanced scalability, stability, and reduced overhead.
Unveiling EIGRP's Revolutionary Impact on Networking
At its core, as one of the sophisticated interior gateway protocols, it leverages the innovative Diffusing Update Algorithm (DUAL). Therefore, it ensures consistent, loop-free routing decisions across even the most complex network topologies. DUAL's ability to quickly adapt to changing network conditions and efficiently calculate the shortest path without compromising efficiency or reliability distinguishes EIGRP from its predecessors.
In 2013, the protocol transitioned to an open standard by releasing basic protocol details. This move enabled broader interoperability and set the stage for its continued evolution. However, it's important to note that while Cisco published information for compatibility purposes, the full implementation details required for creating fully interoperable solutions remained proprietary.
This strategic decision was taken to enhance EIGRP's applicability across a wider range of devices and network scenarios while still maintaining Cisco's core innovations and advantages in its proprietary version. This transition not only underscored EIGRP's resilience and adaptability but also paved the way for broader adoption and a future of continuous improvement.
As we delve into EIGRP's mechanisms and benefits, we'll uncover how it has become an indispensable tool for network professionals seeking to optimize their infrastructure in the face of ever-increasing complexity and demand. EIGRP's dynamic routing capabilities, including its efficient shortest path calculation, and transition to an open standard, underscore its contribution to the advancement of network routing technologies.
Advanced EIGRP Configuration Techniques
Cisco introduces two ways to configure EIGRP: Classic Mode and Named Mode. In classic mode, some of the protocol’s configuration parameters are placed under Interface configuration, and It causes difficulty troubleshooting, but in named mode, most of the parameters are placed in one place, and you do not need to scroll up and forth between the EIGRP process and interface configuration.
Bandwidth Maximization through Wide Metrics
It is important to note that EIGRP's metric calculation underwent a significant change with the introduction of the named mode (EIGRP Named Configuration), which allowed for the adoption of wide metrics. This change was prompted by the increasing bandwidth capacities of modern networks, which exceeded the 1Gbps threshold that classic EIGRP's metric calculations could handle.
Wide metrics expand the scale of EIGRP's metric components and improve the accuracy and efficiency of path selection across interfaces with bandwidths ranging from 1Gbps to 100Gbps and beyond. This enhancement ensures that EIGRP remains relevant and effective in optimizing routing decisions in highly scalable and dynamic network environments.
Streamlining Configuration with Cisco IOS
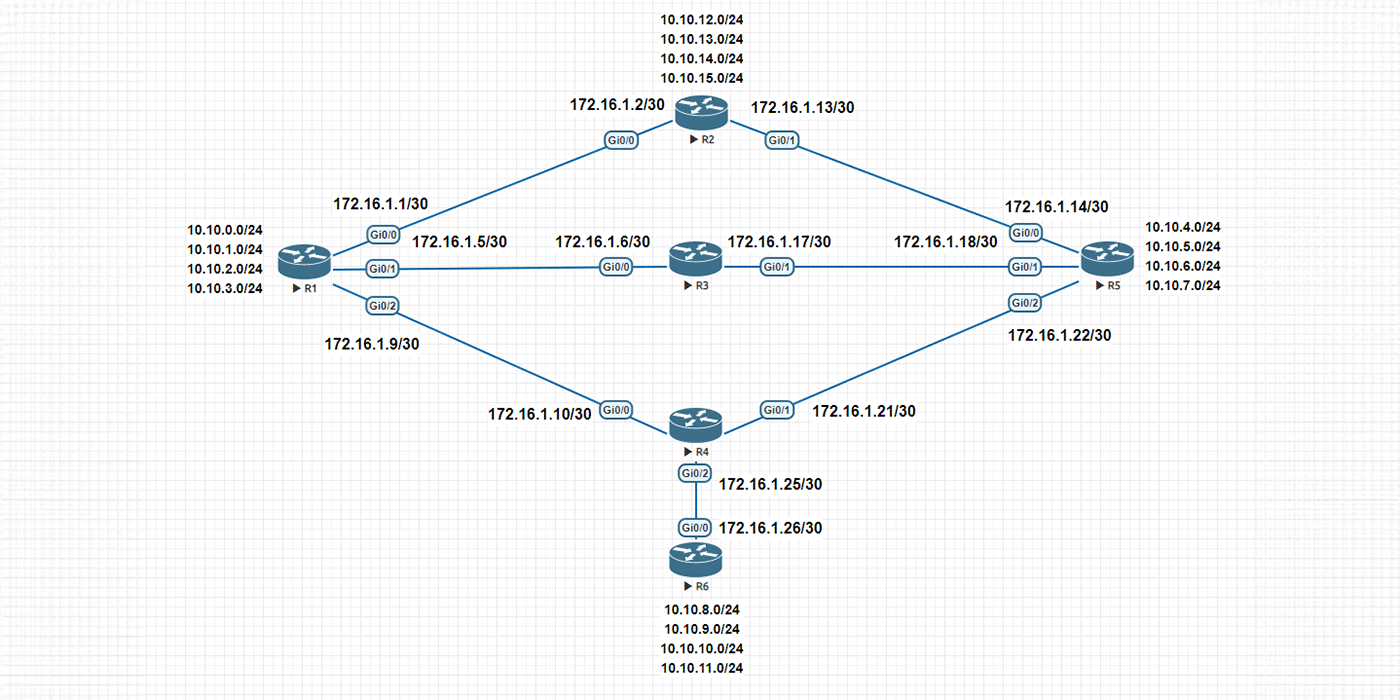
In this document, leveraging Cisco IOS's capabilities, we use the named mode to configure our topology. I used this network diagram to explain.
Understanding EIGRP's Core Mechanisms
The protocol maintains three tables: Neighbor Table, Topology Table, and Routing Table
1. Neighbor Table:
The Neighbor Table includes all neighbors that are directly connected to the EIGRP router. In simple words, next hop router and the interfaces. The neighbor table includes all neighbors that are directly connected to the router using EIGRP. To check neighbors in Cisco IOS, use the command “show ip eigrp neighbors.”
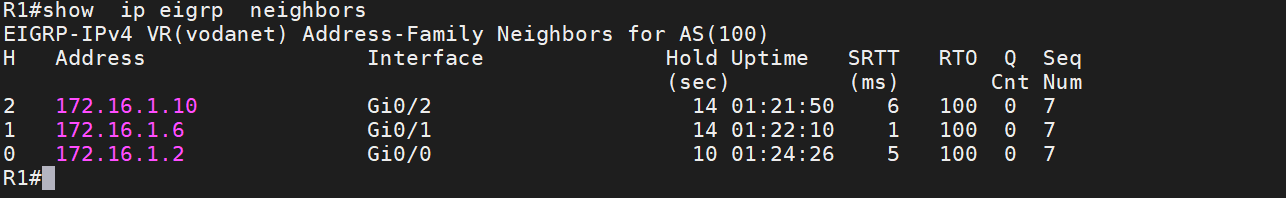
Adjacency is established once the Neighbor Table populates with entries upon receiving a Hello packet from a directly connected router. For instance, when two routers, Router A and Router B, establish communication, Router A, upon receiving a Hello packet through interface GigabitEthernet0/1, adds an entry for Router B in its Neighbor Table. This procedure is vital for establishing and maintaining EIGRP neighbor relationships, which are fundamental for exchanging routes.
2. Topology Table:
To view how EIGRP uses this table to store all routes learned from neighbors, network administrators can utilize the 'show ip eigrp topology' command, which reveals a list of all destinations and routes advertised by neighboring routers.
The EIGRP Topology table contains everything that EIGRP has learned. Use the command show ip eigrp topology. This output has been abbreviated.
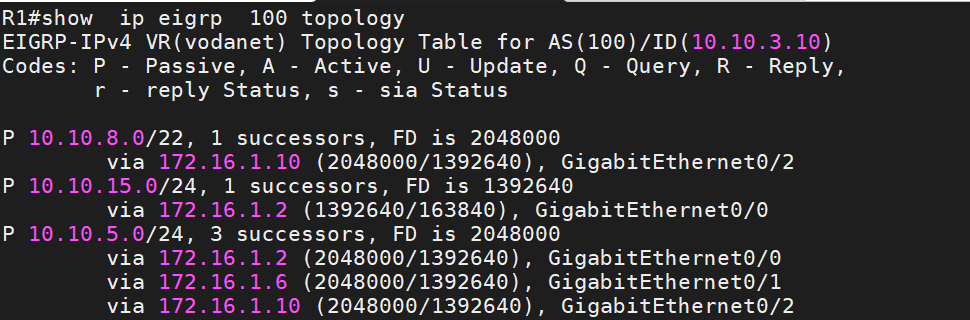
3. Routing Table:
EIGRP stores the single best (Successor) route for each destination in this table. The router uses this table to forward the packet. There is a separate routing table for each routed protocol. Use The command show ip route eigrp
Deep Dive into EIGRP Terminology
· Successor
Next hop for successor route. A Successor route is the lowest metric route to a destination network, while a Feasible Successor is a backup route that satisfies the Feasibility Condition.
· Successor Route
The route with the lowest path metric to reach a destination; this route was installed in the Routing Information Base (RIB). : The total Metric to reach a destination network.
· Reported Distance
The distance a router reports to reach a destination. The RD value is FD for the Advertising router. Each EIGRP Routers Independently calculates its metric.
· Feasibility Condition
The Feasibility Condition is a critical metric ensuring that any backup route reported by a neighbor possesses a metric less than or equal to that of the best-known route, fostering a stable and loop-free routing environment.
· Feasibility Successor
A backup Route was added to the EIGRP topology table, and it has passed the Feasibility Condition and is guaranteed a loop-free path to a destination.
Elevating Network Security and Efficiency with EIGRP
Implementing EIGRP, a key player among interior gateway protocols, is straightforward; you configure EIGRP with the same AS number on all routers and then enable the network command to specify which interfaces to advertise to neighbors. However, it is not a good choice because you encounter problems such as slow convergence time and slow network when your network grows. In this topic, we discuss best practices for the implementation of the protocol.
Fortifying Networks: EIGRP Authentication Unpacked
In network security, it is crucial to pay attention to the importance of implementing authentication mechanisms for EIGRP. Failing to do so can create vulnerabilities in your routing tables and pave the way for potential intruders to disrupt network operations by injecting malicious routes. To ensure the reliability and security of your EIGRP-enabled network, it's essential to develop a strong authentication strategy to guarantee the integrity of your network's data and prevent unauthorized access.
One of the most common configurations network administrators must remember when configuring interior gateway protocols like EIGRP is authentication; it's often overlooked that an attacker could configure a virtual router and advertise incorrect routing information. Cisco suggests configuring EIGRP with authentication to prevent unauthorized or rouge routers from becoming neighbors.
Key Chain vs. Simple Password: Enhancing Security
The protocol uses two modes for configuration authentication: simple password and Key Chain.
Key Chains offer a bastion of security, unlike simple passwords, which can fall prey to brute force attacks due to their often simplistic nature. They allow for the creation of longer and far more complex keys, drastically enhancing protection against unauthorized access attempts. This complexity significantly elevates the network's defense against cracking efforts.
The below section shows the commands necessary to configure EIGRP authentication with Key Chain.
R1#configure terminal
R1(config)#key chain networkdevkey
R1(config-keychain) #key 1
R1(config-keychain-key) #key-string networkdev
R1(config-keychain-key) # exit
R1(config-keychain) # exit
R1(config)#router eigrp networkdev
R1(config-router) #address-family ipv4 unicast autonomous-system 100
R1(config-router-af) #af-interface default
R1(config-router-af-interface) #authentication mode md5
R1(config-router-af-interface) #authentication key-chain networkdevkey
R1(config-router-af-interface) #end
Authentication must be configured for all neighbors; if it does not match between two neighbors, the protocol doesn't form a neighbor adjacency. In the configured key chain, networkdevkey is just a name; this name can be different on all routers, but for simplicity, it is better to use the same name.
Two important things that must be matched in the EIGRP Domain are key ID (id can be 0-2147483647) and key-string.
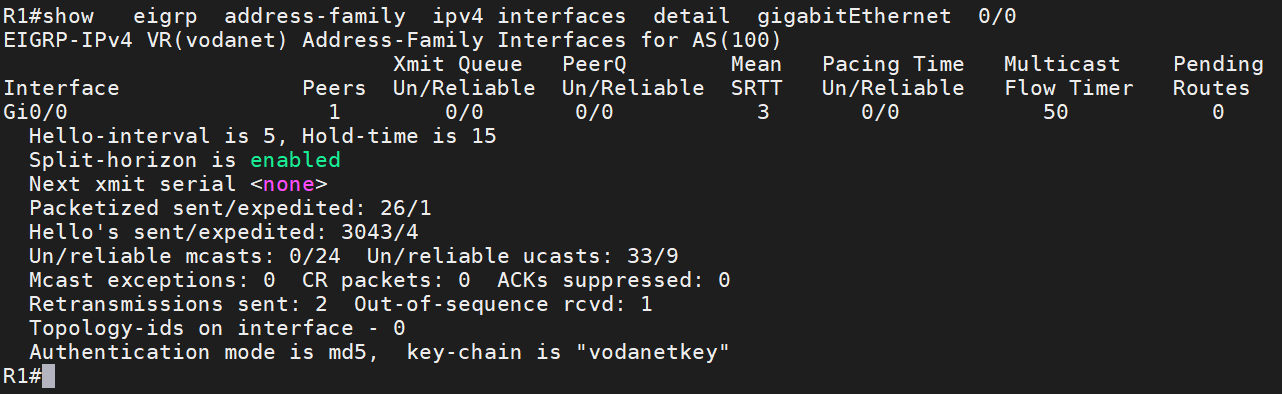
Authentication can be applied to an interface or by default, affecting all interfaces participating in the protocol. Command show eigrp address-family ipv4 interfaces detail gigabitEthernet 0/0 verify specific interface.
Implementing EIGRP Passive Interfaces
The primary purpose of configuring a passive interface in EIGRP is to prevent the router from sending routing updates out of that interface while still allowing the router to receive updates on that interface. This can help improve network efficiency and security.
For example, you have an interface toward the clients. Because this interface is the default gateway and you don’t have a router or switch in the segment, you can configure the interface as a passive interface. This section shows the commands necessary to configure the EIGRP Passive interface.
R1#configure terminal
R1(config)#router eigrp networkdev
R1(config-router) #address-family ipv4 unicast autonomous-system 100
R1(config-router-af) #af-interface loopback0
R1(config-router-af-interface)# passive-interface
Note: When you configure the interface as passive, it participates in the EIGRP process but prevents EIGRP from receiving hello on the interface. If you run the command show ip eigrp interface, you can see EIGRP enabled on the Interface loopback0, but it does not send and receive a hello message. This command does not show if an interface was configured as passive.
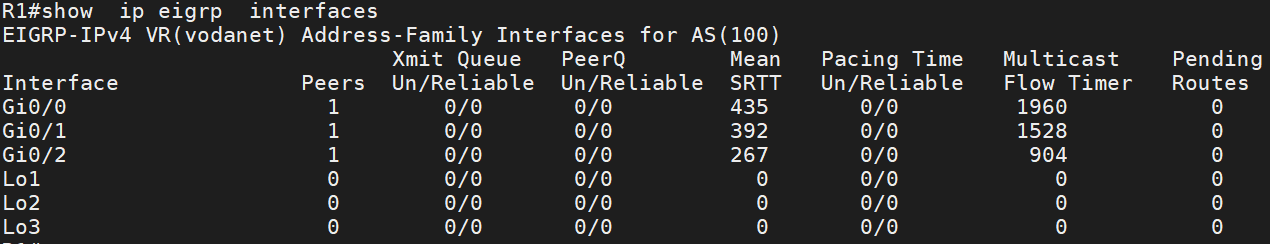
to check which interface is configured as passive, use the command show ip protocols | section Passive
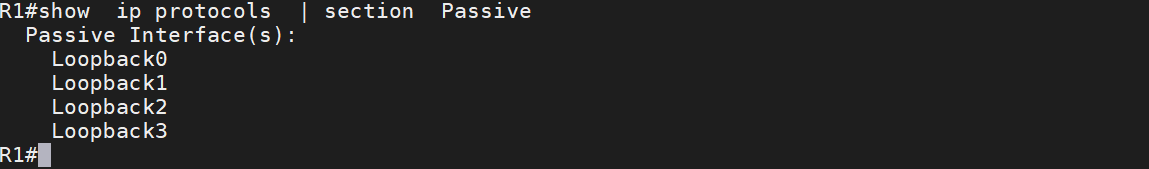
You can configure the passive-interface for a specific interface or configure the passive-interface for all interfaces and then exclude a particular interface with the command no passive-interface.
R1(config)#router eigrp networkdev
R1(config-router) #address-family ipv4 unicast autonomous-system 100
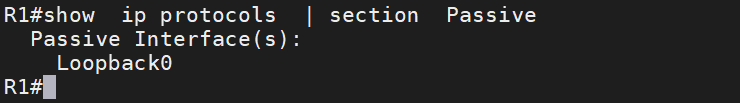
R1(config-router-af) # af-interface default
R1(config-router-af-interface) # passive-interface
R1(config-router-af-interface) #exit
R1(config-router-af) #af-interface gigabitEthernet0/0
R1(config-router-af-interface) #no passive-interface
Route Summarization and Passive Interfaces
Route Summarization can be done manually or automatically, but Cisco suggested using manual route summarization. Route summarization refers to aggregating multiple specific routes into a single summary route. This can be useful for optimizing routing tables, reducing the routing information's size, reducing CPU and memory resource consumption, and improving network efficiency.
With the summary-address command, the protocol supports manual route summarization at the interface level. Summary routes are always advertised based on the outgoing interface.
Route summarization is a technique used in EIGRP that combines several routes into a single summary route. By doing so, the size of the routing table is reduced, which in turn decreases the memory usage and CPU processing time, enhancing the overall network performance and scalability.
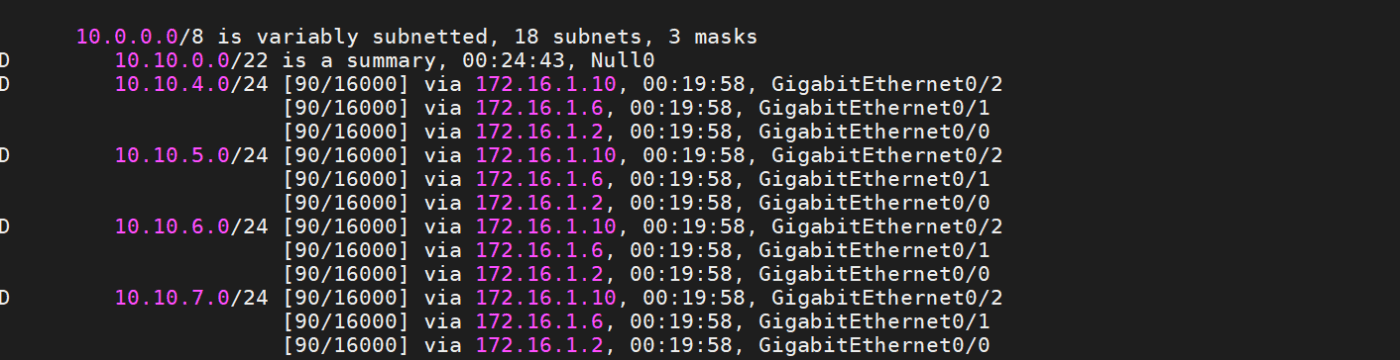
The below section shows the commands necessary to configure EIGRP Manually Route Summarization. Before going deep into route summarization, I showed the R3 routing table. This output is abbreviated for simplicity. I configured route summarization at R1, R5, R6.
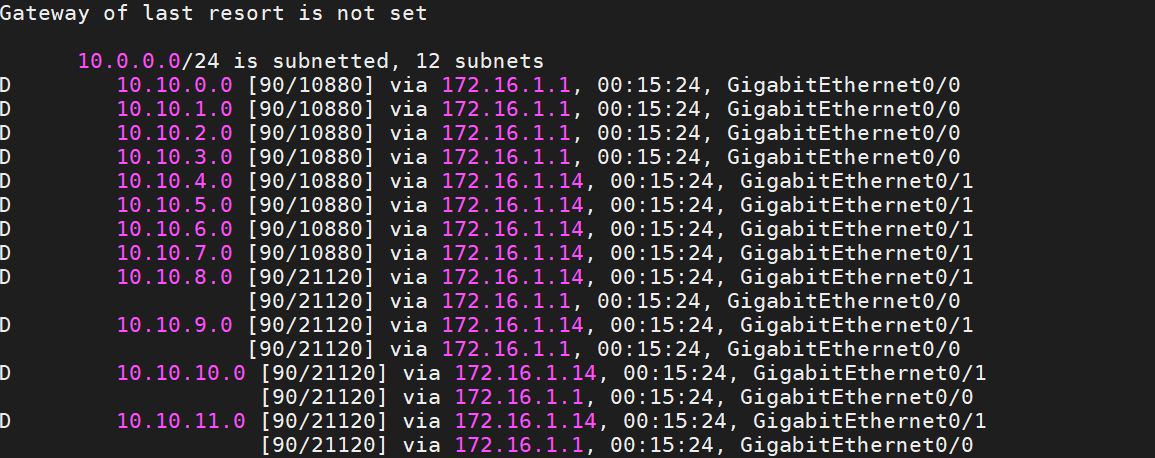
R1(config)#router eigrp networkdev
R1(config-router) #address-family ipv4 unicast autonomous-system 100
R1(config-router-af) #af-interface gigabitEthernet0/0
R1(config-router-af-interface) #summary-address 10.10.0.0/22
R1(config-router-af-interface) #exit
R1(config-router-af) #af-interface gigabitEthernet0/1
R1(config-router-af-interface) #summary-address 10.10.0.0/22
R1(config-router-af-interface) exit
R1(config-router-af) #af-interface gigabitEthernet0/2
R1(config-router-af-interface) #summary-address 10.10.0.0/22
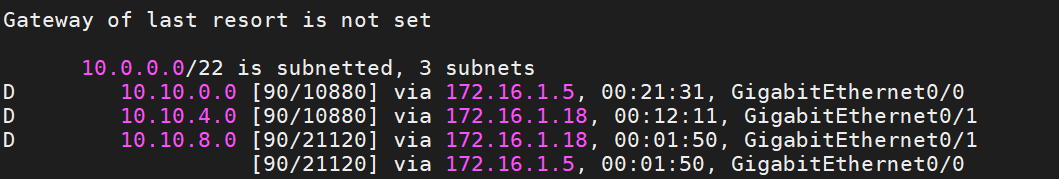
Leveraging EIGRP Stub Routing for Efficient Remote Networking
Within the realm of interior gateway protocols, a stub router refers to a device lacking complete routing information about the network. EIGRP stub routing is a feature that allows you to simplify the network design by configuring certain routers as stub routers. This is often done in remote or branch offices to reduce the amount of routing information that needs to be maintained.
A stub router does not advertise routes learned from other peers within the protocol. By default, EIGRP stubs advertise only connected, and summary routes and a router as a stub router will not receive queries from other routers, and it is an excellent technique to stop query traffic.
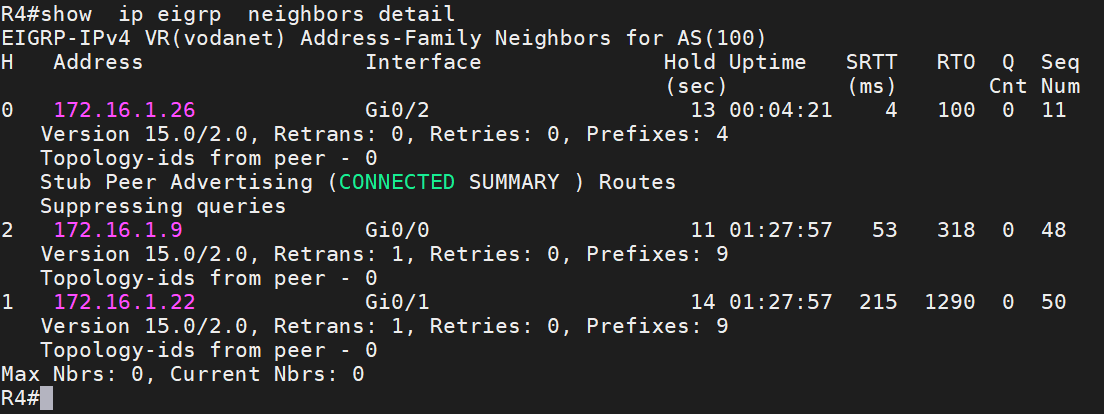
For example, consider a loopback0 of router 2 going down; R2 immediately sends a query message to all routers in AS 100 to find an alternative path to loopback0. IN Our topology, R6 has R4 as a neighbor; it does not need to process query messages from R2 because it doesn’t have an alternative path.
To configure a router as a stub router, we use the command eigrp stub and define the connect and summary options; these two options cause the stub router to advertise connected and configured routes. The command shows ip eigrp neighbor detail shows R4 suppressed query message toward R6.
Architecting Hierarchical Networks with EIGRP
Unlike OSPF, EIGRP does not have an area. Distance vector routing protocols such as EIGRP hide routing information in topology. When you configure EIGRP without ANY OPTIONS, it is like OSPF, meaning you configure all routers in area 0.
In an EIGRP network, hierarchy is created through summarization. EIGRP has no imposed limit on hierarchy levels, which can be its vital design advantage. I created a new 3-layer network (Core, distribution, and access) to show how to implement route summarization in hierarchical architecture.
Still, before going deep, we must familiarize ourselves with choke points and zones. According to the Cisco website, a zone is simply a group of network devices (Switches or routers) with many connections between each other. Typically, it may be a site or a building.
Zones are topologically defined parts of the network. Zones define a failure domain link, and device failures in a zone should have little or no impact outside a specific zone.
Instead, a choke point is placed between zones so that the only way from one zone to another is via one or two choke points Or simply a place between zones. For example, a choke point exists between Zone-1 and distribution layer-1. We can summarize the address from zone-1 toward distribution layer-1.
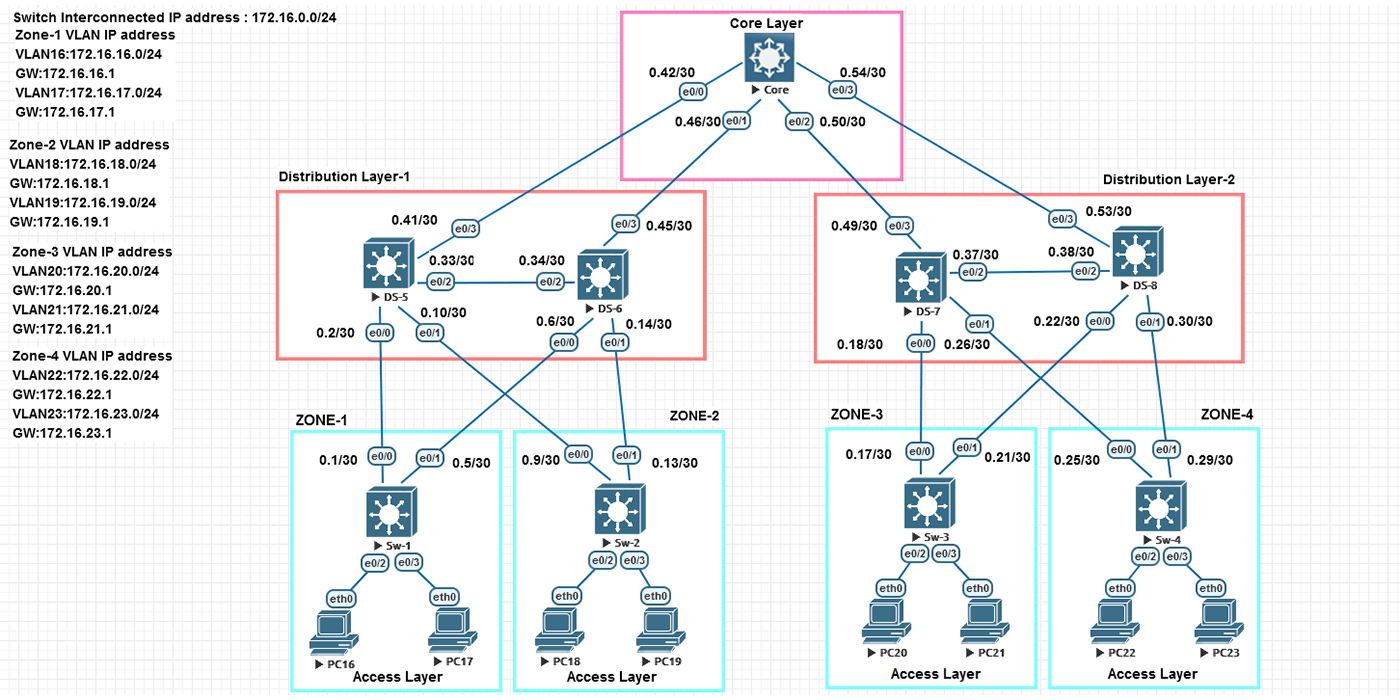
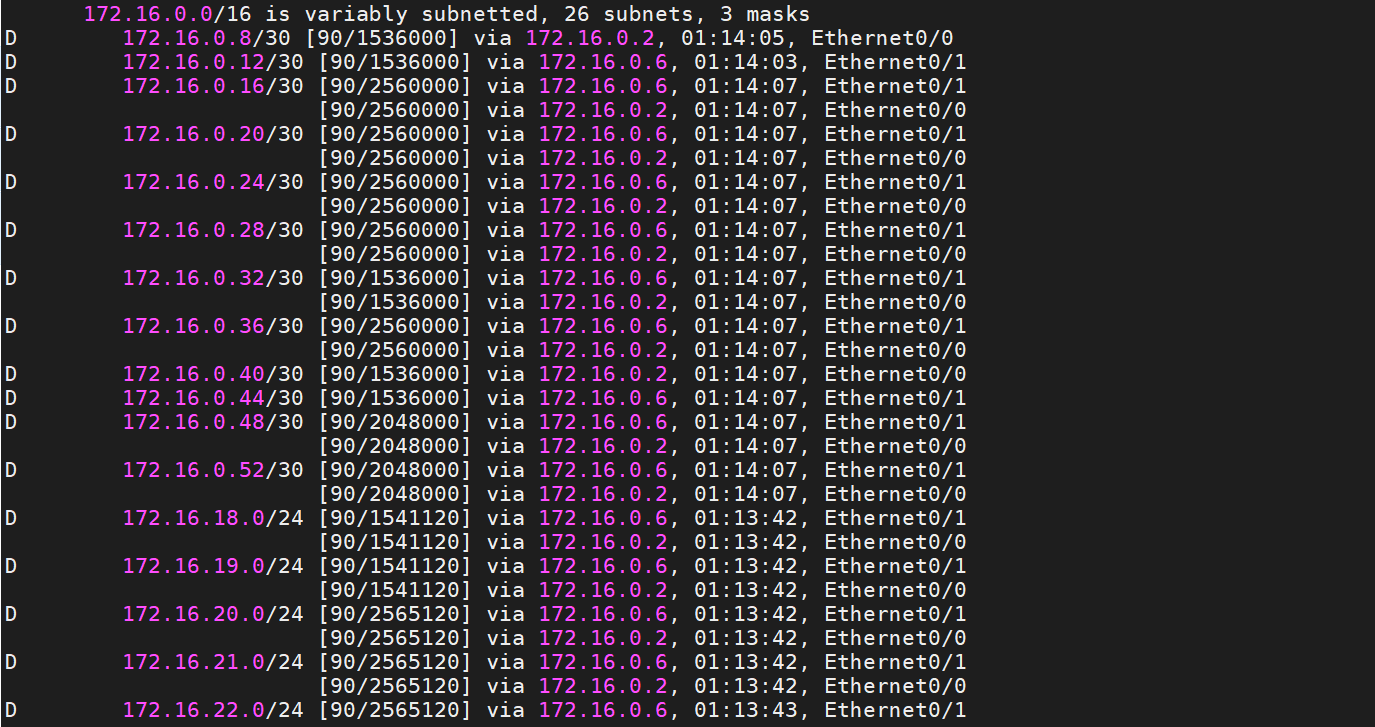
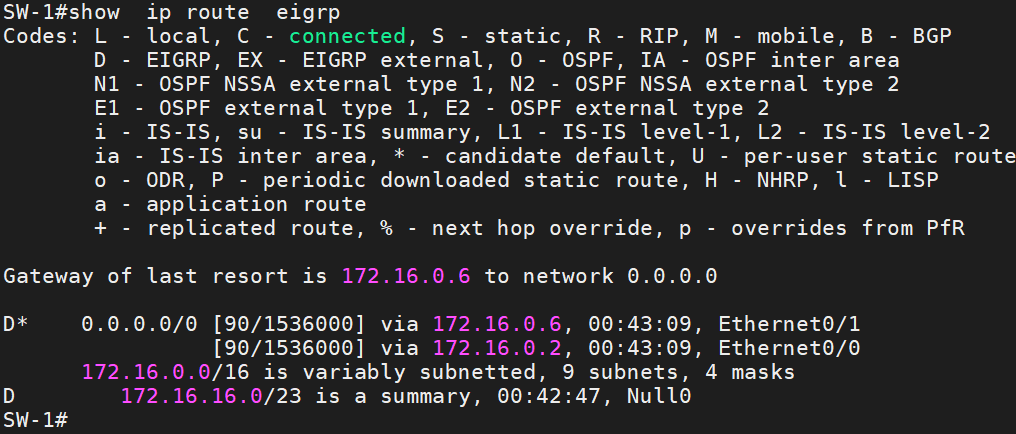
I configure zone-1 until zone-4 as the routed Access layer. All interfaces from Zones 1 to 4 are configured as layer 3 interfaces. I configured EIGRP on all devices. Before configuring route summarization, I will show you the routing table from SW-1.
Another option I configured is the Stup Area. Zones 1 through 4 are configured as stub areas. for example, I configured summary address at SW-1’s eth0/0 and eth0/1 toward DS-5 and DS6 and on DS-5 and DS-6 configured default route as summary address toward SW-1 and SW-2. Before configuring the summary address, we had 26 subnets in SW-1, and now we have just a default route with ECMP (Equal Cost Multi-Path).
The Summary Address below was configured at SW-1 toward DS-5 and DS-6.
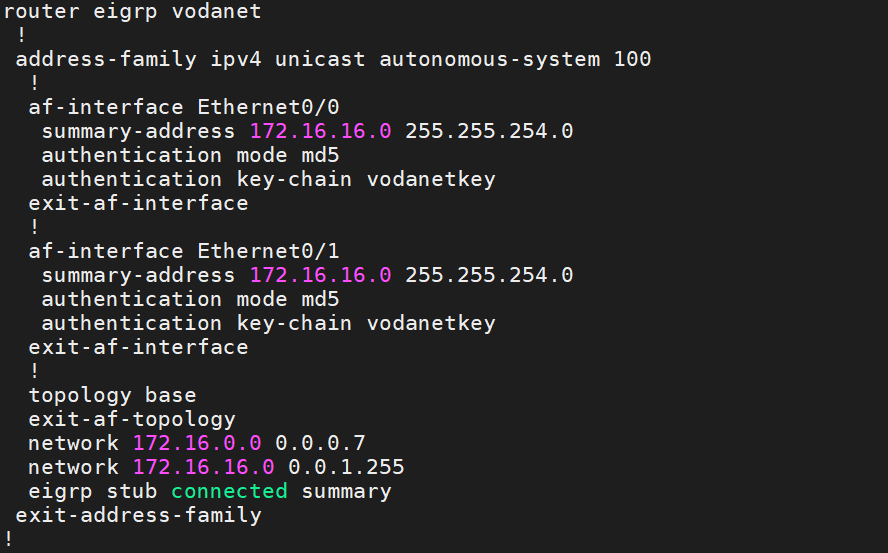
The Summary Address below was configured at DS-5 and DS-6 toward SW-1 and SW-2.
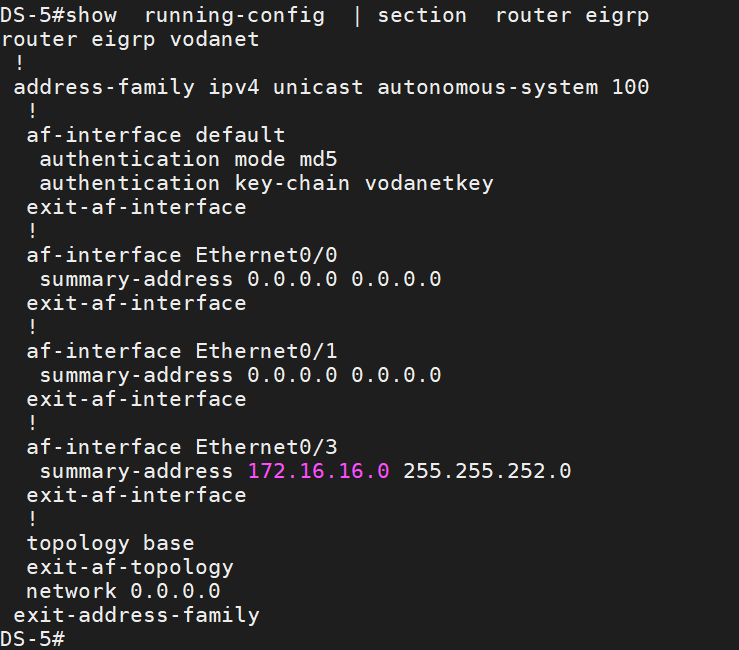
After Configuring the Summary Address, we have just the default route toward DS-5 and DS-6 with ECMP.
Another option for EIGRP hierarchical configuration is to configure multiple AS numbers in our topology. For example, we can put each layer in one AS number. Cisco doesn’t recommend this setting, but we can use multiple AS numbers for situations like:
§ Migration strategy after a merger or acquisition.
§ They support different domains of trust or administrative control.
When you use the routed Access layer, all configurations for the layer 2 Access layer move from the distribution layer to the access layer, and the Spanning-tree Algorithm stays in the access layer. You have better convergence time and can use the benefits of ECMP. We can configure the hello interval and hold-timer of eigrp to 1 and 3 secs for faster convergence time.
Below, I created a mind map for EIGRP that shows its most important characteristics:
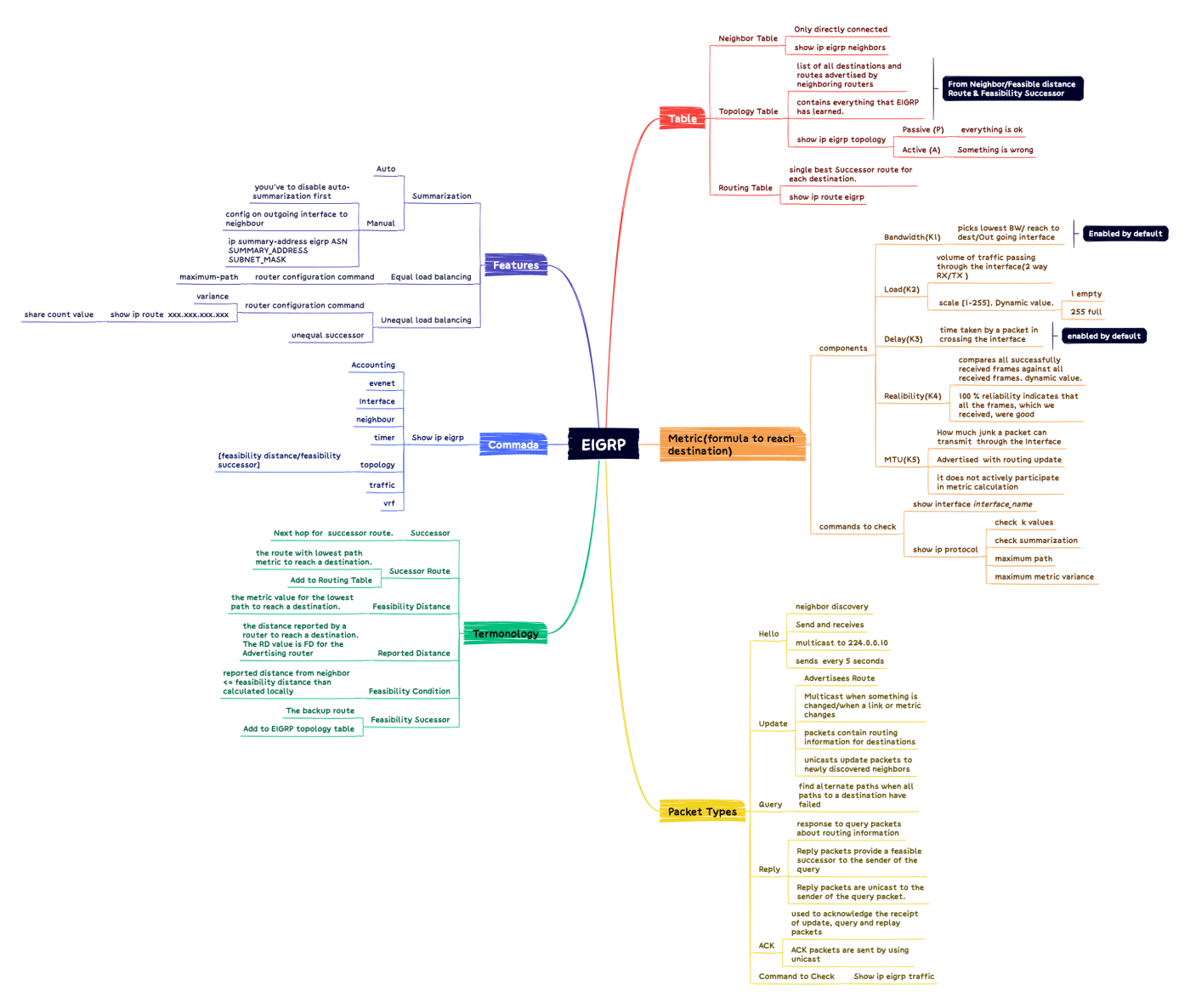
Key Takeaways for Future-Proof Network Design
EIGRP is a highly valuable protocol for network design, offering speed, reliability, and flexibility. It ensures efficient and loop-free routing for complex topologies through its innovative Diffusing Update Algorithm (DUAL).
The protocol's evolution into an open standard has broadened its usage, making it even more significant in networking. EIGRP is excellent at optimizing bandwidth, achieving fast convergence, and simplifying management, making it scalable for networks of all sizes.
For network designers, utilizing EIGRP means prioritizing structure, performance, and scalability, as well as following best practices to improve security and efficiency. In essence, EIGRP gives networks the resilience and adaptability they need to thrive in today's ever-changing digital landscape.