You have no items in your shopping cart.
Best Practices for Layer 3 Routing Selection in Large-Scale Networks
Are you seeking to optimize your large-scale network's performance and security? Enhance your network's capabilities with this guide, which explores advanced Layer 3 routing strategies. It delves into protocol selection, hierarchical design principles, and optimizing network infrastructure for robust, efficient, and secure operations. Network designers can make more informed decisions for their network architectures by using these insights, leading to greater efficiency and security. This technical exploration empowers you with the knowledge needed for unparalleled network management and security.
Effective Layer 3 routing is vital in large-scale networks to ensure seamless communication, optimal performance, and scalable connectivity. Layer 3 routing involves exchanging routing information between Layer 3 devices in the network to determine the best paths for data transmission, playing a critical role in directing traffic across widespread networks. Implementing best practices is necessary to achieve the desired level of reliability, efficiency, scalability, and security in large-scale environments.
A Hierarchical Network is one of the most critical requirements before using best practices for Layer 3 routing. This network topology divides a flat network topology into 2 or 3 layers, depending on the size of users. It provides visibility to the overall network for the network designer and enables them to choose the right network devices for each layer.
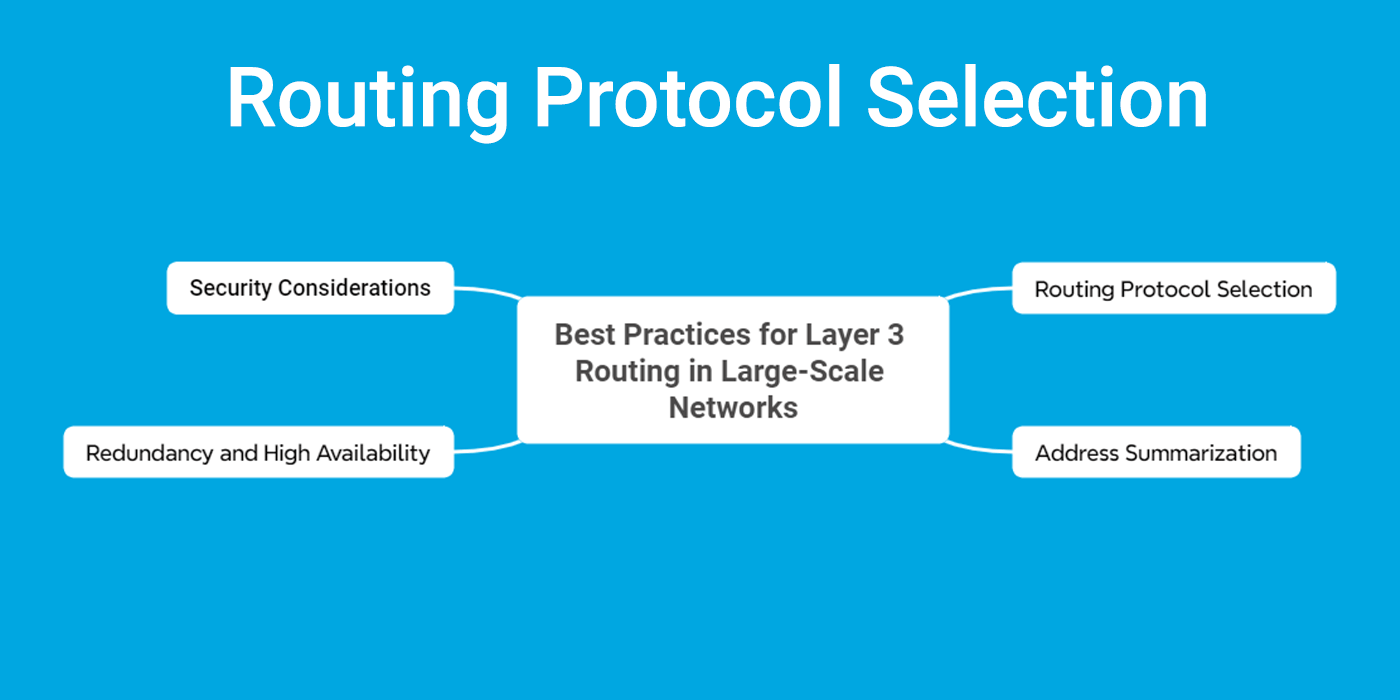
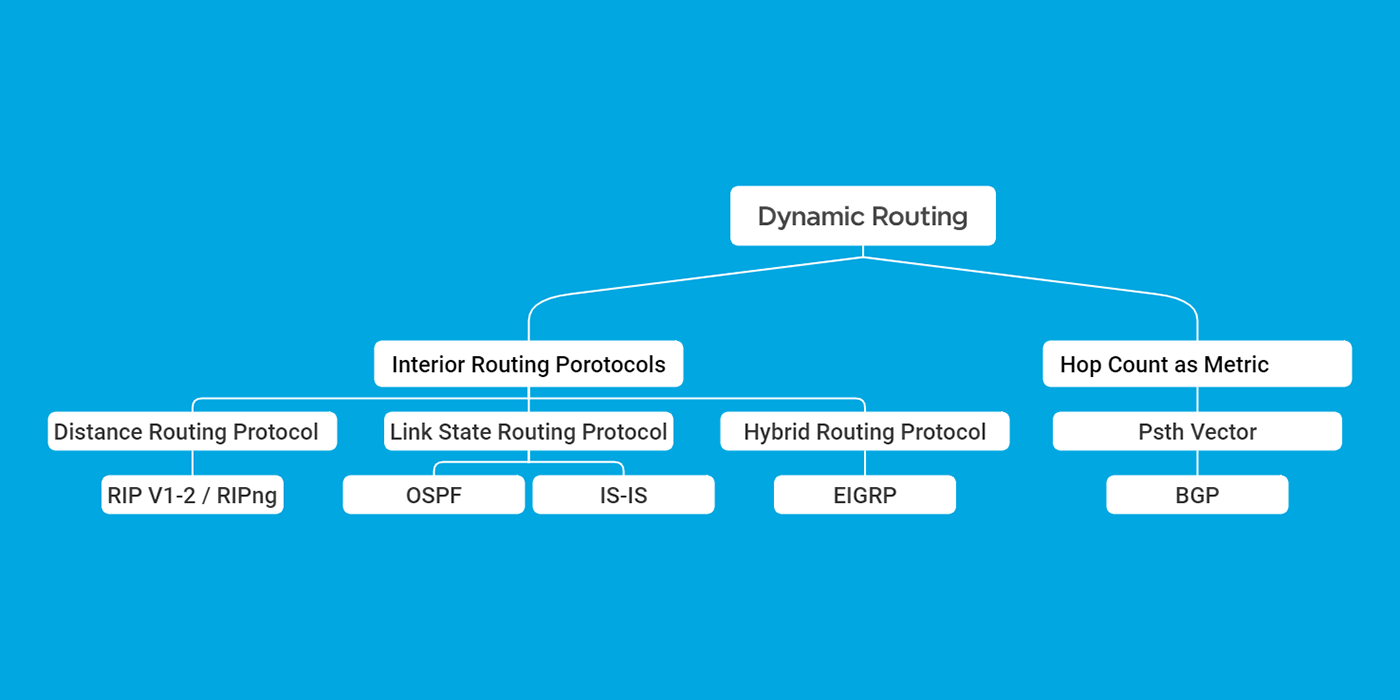
We discuss hierarchical network design on a different topic in the future. For the implementation of Best Practices for Layer 3 Routing in Large-Scale Networks, we can follow this Mind Map.
Layer 3 Routing Protocol Selection
A routing protocol is nothing but a set of rules that determine how Layer 3 devices such as Routers, Firewall, and Layer 3 Switches communicate with each other to exchange information about network paths or Network topology using IP addresses and make decisions on the most efficient routes (Best Path) for data to travel between devices on a computer network (Between Source and Destination). These protocols play a fundamental role in the functioning of the Internet and other interconnected networks.
Routing protocols are fundamental to computer network operation, guiding data flow between devices and determining the most efficient paths for communication. Selecting the appropriate routing protocol is a critical decision that significantly influences network performance, scalability, and resilience.
The choice of a routing protocol depends on various factors, including the network's size, complexity, Network Devices, and specific requirements. This process, known as Routing Protocol Selection, involves careful consideration of the characteristics and capabilities of different routing protocols to ensure they align with the organization's goals and network architecture.
Routing Protocol Classification
Routing protocols are classified based on their use, scope, and the way they exchange routing information, including IP addresses. These classifications help network administrators manage effectively by choosing the most suitable routing protocol for a particular network environment. Before deepening into Routing Protocol Classification, we must be familiar with the Autonomous System (AS) concept. According to Wikipedia, an Autonomous System is a collection of network devices and Internet Protocol (IP) controlled by one organization.
Another term is a Routed Protocol. A crucial aspect of a Routed Protocol is its use of IP addresses to deliver user data (packets) from the source to the Destination across a network.
Routed protocols are designed for addressing and forwarding data packets. These protocols determine the logical addressing scheme, such as IPv4 and IPv6 addresses, and define how data packets should be encapsulated, addressed, and routed in a network.
Routed protocols operate at the OSI model's network layer (Layer 3). Now, let's provide an introduction to the primary classifications of routing protocols:
Routing Protocols are divided into 2 different Categories: Interior Gateway Protocol(IGP) and Exterior Routing Protocol(EGP).
1. Interior Gateway Protocol (IGP):
Interior Gateway Protocols operate within a single autonomous system (AS), a collection of networks under a common administration. IGPs are used inside a computer network(Organization's Network ) and are limited to the border router.
OSPF, a dynamic Internet Gateway Protocol, is widely recognized for its efficiency in large-scale enterprise networks. It is known for its ability to scale and fast convergence time. OSPF's hierarchical system with areas is designed to manage complex topologies, reducing the overhead on individual routers and improving network stability. This protocol is particularly advantageous in environments requiring rapid routing information updates and supports both IPv4 and IPv6 networks.
2. Exterior Routing Protocol (EGP):
Operate between different autonomous systems, typically at the boundaries of the Internet. In EGP, we have the Border Gateway Protocol (BGP). BGP is the core of Internet layer 3 routing protocols.
In this topic, we focus on IGP, utilizing IP addresses for internal routing, because Interior Gateway Protocols are essential for the effective management, scalability, security, and reliability of an organization's internal network. These protocols are necessary for internal routing within the network infrastructure, enabling efficient communication among connected devices within the same network.
BGP, utilizing IP addresses, serves as the backbone of the internet routing system, managing data paths between different autonomous systems (AS). It is essential for networks that require control over routing paths for performance, security, or policy reasons.
BGP's strength lies in its extensive path attributes, which offer unmatched flexibility and control for large-scale, internet-connected networks.
Interior Gateway Protocol(IGP):
There are several types of Interior Gateway Protocols, each with its own characteristics and use cases. The three main types of IGPs are Distance Vectors, Link-State protocols, and Hybrid Routing Protocols. Hybrid layer 3 routing protocol is a combination of distance routing protocol and link-state routing protocol. In the Interior Gateway Protocols (IGP) context, EIGRP is considered a Hybrid dynamic Routing Protocol.
EIGRP is a routing protocol developed by Cisco that combines the benefits of distance vector and link-state protocols. It is known for its fast convergence, low bandwidth usage, and ability to support large and complex networks. EIGRP is highly efficient in calculating the best path with minimal overhead, making it an attractive option for networks of varying sizes.
Additionally, EIGRP supports route summarization, unequal cost load balancing, and easy configuration, making it a versatile routing protocol for modern networks.EIGRP is a routing protocol developed by Cisco that combines the benefits of distance vector and link-state protocols. It is known for its fast convergence, low bandwidth usage, and ability to support large and complex networks.
EIGRP is highly efficient in calculating the best path with minimal overhead, making it an attractive option for networks of varying sizes. Additionally, EIGRP supports route summarization, unequal cost load balancing, and easy configuration, making it a versatile routing protocol for modern networks.
Distance Vector Routing Protocol:
Before we dive into Distance Routing Protocol, let me ask a question about the meaning of the word "Rumor." According to the Longman Online Dictionary, it is defined as information or a story passed from one person to another that may or may not be accurate. Keep this definition in mind until the end of this topic.
A Distance Vector routing protocol applies both distance (metric value/hop count) and direction (vector/ outgoing Interface) to determine the optimal path to the destination network. Routers in this protocol receive updates from neighboring routers, which continue until reaching the destination network. Each router along the path to the Destination is referred to as a hop, and as a packet travers router, the hop count value increases. The route with the least hop count is selected as the best path and is added to the routing table.
Examples of Distance Vector routing protocols include RIP version 1 and RIP version 2, both of which share the entire routing table with directly connected neighbors. However, Distance Vector Layer 3 Routing Protocols are known for being relatively slow and having the potential for loops. The term "distance" indicates how far away, while "vector" means the direction (outgoing Interface) in this context.
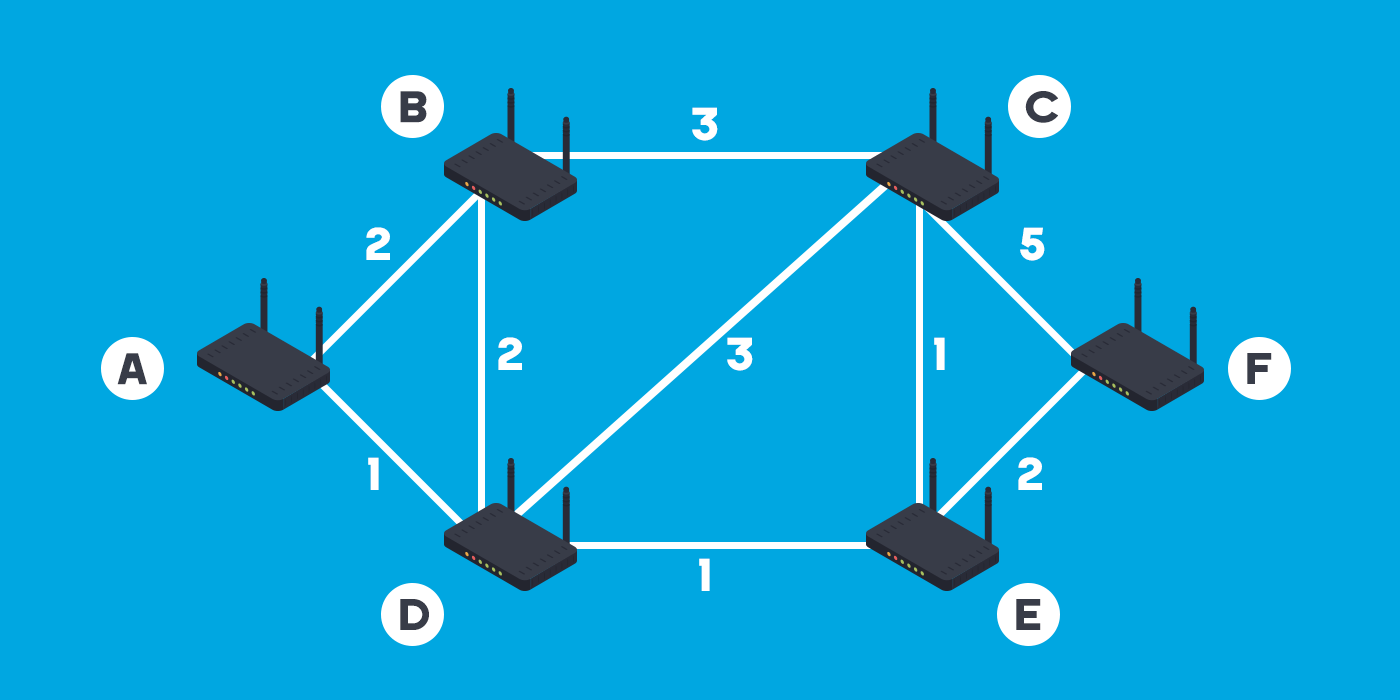
Distance Vector Routing Protocols, such as RIP (Routing Information Protocol), send updates to neighboring routers using periodic broadcasts or triggered updates. The process involves routers sharing information about their routing tables, allowing each router to understand the network topology. Key features and characteristics of Distance Vector Routing Protocols include:
I. Hop Count as Metric:
Distance Vector protocols, such as RIP (Routing Information Protocol), use hop count as their metric. The number of hops (intermediate routers) to reach a destination is the primary factor in determining the best path. For example, the maximum hop count for RIP is 15, and 16 is used to represent an infinite route.
II. Periodic Updates:
Routers using Distance Vector protocols exchange routing information with their neighbors at regular intervals. These periodic updates inform routers about the network topology and any changes in routes.
III. Simplicity:
Distance Vector protocols are generally simpler to implement and understand than other routing protocols. This simplicity can be an advantage in small to medium-sized networks.
IV. Routing Table:
Each router maintains a routing table including information about known destinations, the next-hop router, and the associated metric (hop count).
V. Convergence Time:
One drawback of Distance Vector protocols is their slower convergence time. Changes in the network, such as link failures, take some time to propagate through the network and for routers to update their routing tables.
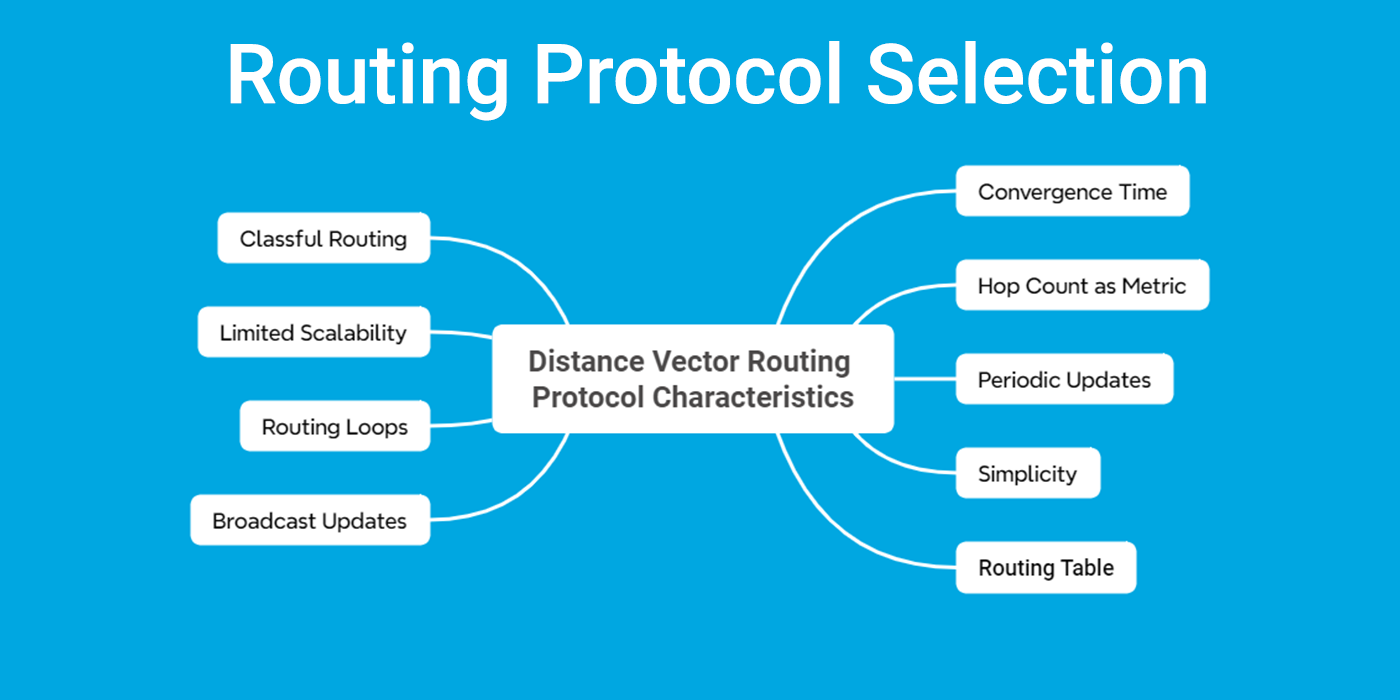
VI. Broadcast Updates:
In some Distance Vector protocols, routers broadcast their layer 3 routing tables to neighboring routers. This broadcast process contributes to the periodic update mechanism.
VII. Routing Loops:
Distance Vector protocols are susceptible to routing loops, where routers continuously exchange outdated information, leading to suboptimal routing decisions. Techniques like split horizon and route poisoning are used to mitigate routing loops.
VIII. Limited Scalability:
Due to their periodic update mechanism and slower convergence, Distance Vector protocols may face scalability challenges in large networks. Rapid changes can result in increased network traffic.
IX. Classful Routing:
Distance Vector protocols typically operate in a classful routing environment, where subnets within a network must use the same subnet mask. This contrasts with classless routing protocols that support Variable Length Subnet Masking (VLSM).
Cisco compares the Distance Routing Protocol to a road sign that a driver mindlessly uses to reach the Destination without knowing whether there is a shorter or better way or whether the sign is correct.
At the beginning of this topic, I asked a question about the word "Rumor." Distance Vector Routing Protocols are likened to routing by rumor (gossip). Each router advertises routes based on its own perspective rather than the original route advertised by the neighbor router. This means that each router has second-hand information about routes in the network. Therefore, a distance vector protocol does not have a complete map of the entire network.
Link-State Routing Protocol
A Link-State Routing Protocol is a layer 3 routing protocol used in computer networks to determine the best path for routing data between devices. Unlike Distance Vector protocols, Link-State protocols maintain a detailed and up-to-date map of the network's topology and use the bandwidth of the Interface as cost. This map, often represented as a link-state database, contains information about the state of each router's directly connected links.
As a router receives advertisements from a neighbor, it stores the information in a local database called the Link State Database (LSDB). It advertises the link-state information precisely as received by each of its neighboring routers. The link-state information propagates throughout the network unchanged, from router to router, just as the originating router advertised it. This allows all routers in the network to have a synchronized and consistent map of the network.
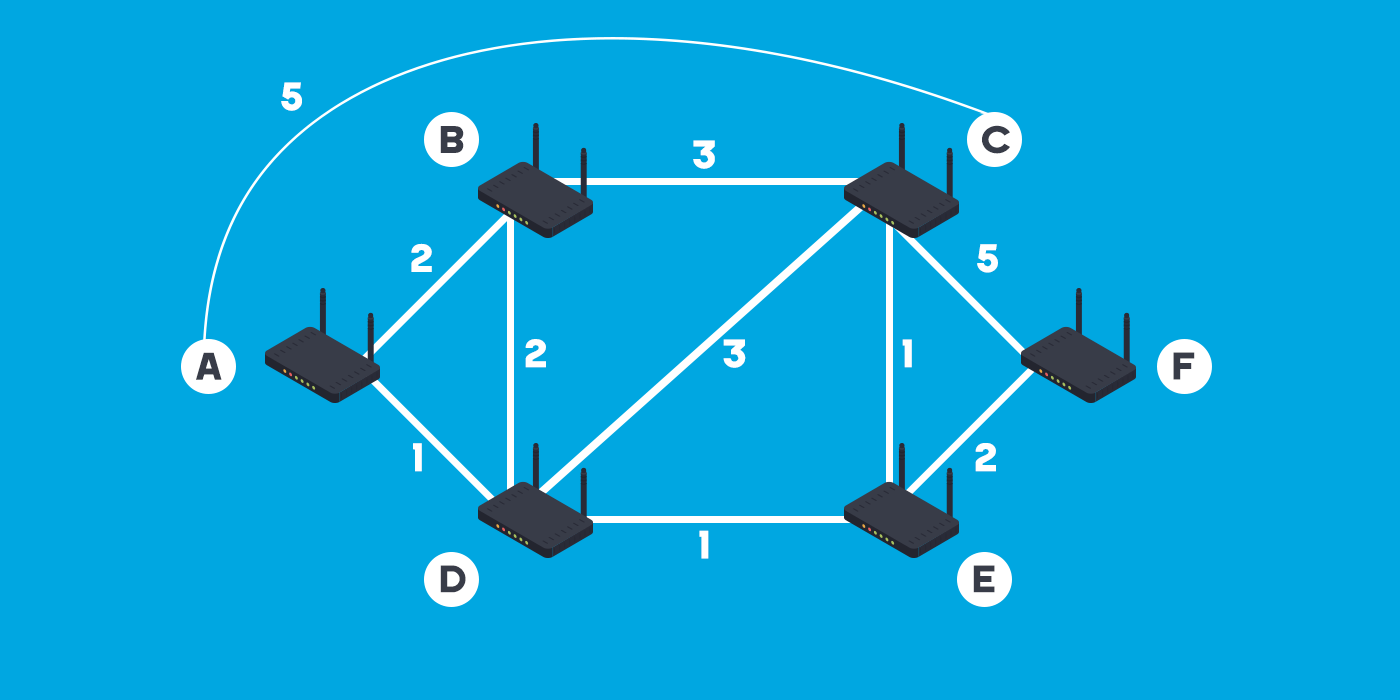
Like Distance Vector routing protocols, Cisco compares link-state routing protocols to a GPS Navigator. In this analogy, the driver has a complete map from the source to the Destination, enabling them to choose the best path (shortest path) to the Destination right from the start of the trip. Key features and characteristics of Link-State Layer 3 Routing Protocols include:
i. Topology Mapping:
Link-state protocols create a comprehensive network topology map, including information about routers, links, and their states.
ii. Link-State Advertisements (LSAs):
Routers within the network exchange Link-State Advertisements, which contain detailed information about the state of their directly connected links. LSAs are used to update the link-state database.
iii. Dijkstra's Shortest Path Algorithm:
Link-state protocols use Dijkstra's algorithm to calculate the shortest path to each Destination based on the link-state database. This ensures efficient and optimal routing.
iv. Database Synchronization:
All routers maintain synchronized link-state databases, allowing them to have a consistent and accurate network topology view.
v. Hierarchical Structure:
Many Link-State protocols support a hierarchical network structure, dividing the network into areas. This helps reduce complexity and improve scalability.
vi. Fast Convergence:
Link-state layer 3 routing protocols respond quickly to changes in the network, leading to faster convergence compared to Distance Vector protocols.
vii. Hello Packets:
Routers in a Link-State protocol exchange "Hello" packets to establish and maintain neighbor relationships. These packets are crucial for detecting changes in the network and maintaining connectivity.
viii. Support for Variable-Length Subnet Masking (VLSM):
Link-state protocols can accommodate Variable-Length Subnet Masking (VLSM), allowing for more efficient use of IP address space.
ix. Path Computation at Each Router:
Unlike Distance Vector protocols, where path computation is distributed, Link-State protocols perform path computation at each router based on the network's detailed map.
Examples of Link-State Routing Protocols include OSPF (Open Shortest Path First) and IS-IS (Intermediate System to Intermediate System). These protocols are commonly used in large and complex networks where accurate information about the network topology is crucial for efficient and reliable routing.
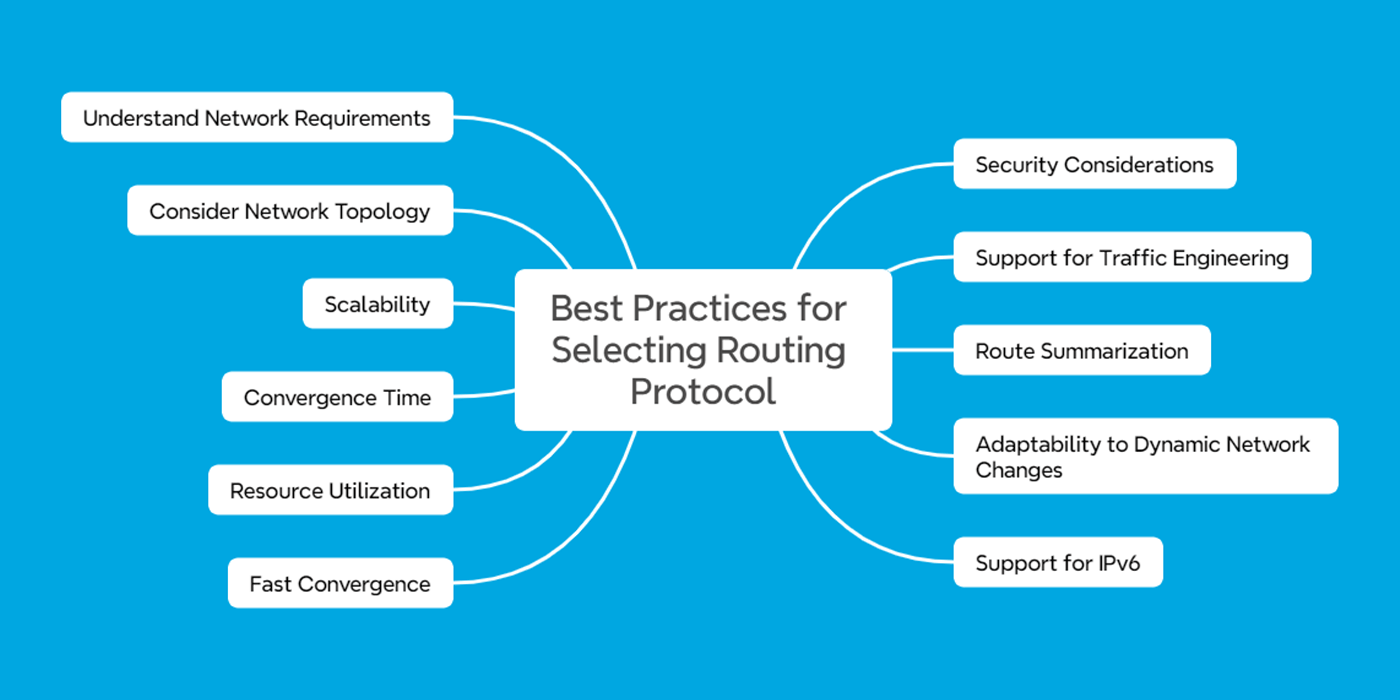
Best practices for selecting Routing Protocol
Selecting the right layer 3 routing protocol and strategy is crucial for designing a robust and efficient network. The foremost factors influencing the choice of the best routing protocol are the knowledge and experience of the network designer. Now, I will explain some tips.
1. Understand Network Requirements:
Begin by thoroughly understanding the specific requirements of your network, including size, complexity, traffic patterns, scalability needs, and any special considerations such as security or Quality of Service (QoS).
2. Consider Network Topology:
Choose a layer 3 routing protocol that aligns with the network's topology. For example, link-state protocols like OSPF are well-suited for complex and hierarchical networks, while EIGRP or BGP may be appropriate for more scalable and diverse topologies.
3. Scalability:
Evaluate the scalability of the routing protocol to ensure it can handle the size of your network, both in terms of the number of routers and the volume of routing information.
4. Convergence Time:
Assess the convergence time of the routing protocol. Faster convergence is critical for minimizing downtime in the event of network changes or failures.
5. Resource Utilization:
Consider the resource utilization of the routing protocol. Some protocols may be more resource-intensive, so choose one that aligns with the available hardware resources. For example, Link-State routing protocols consume more resources than Distance Vector Routing Protocols because they keep the entire network topology in their databases.
6. Vendor Interoperability:
If your network includes equipment from multiple vendors, choose routing protocols that are widely supported and interoperable across different devices. For example, Fortigate does not support EIGRP.
7. Security Considerations:
Evaluate the security features of the routing protocol. Some protocols may offer built-in encryption or authentication mechanisms to secure routing information.
8. Support for Traffic Engineering:
If traffic engineering is a concern, choose a layer 3 routing protocol that supports this feature. Intermediate System to Intermediate System (IS-IS) is a link-state routing protocol commonly used in large-scale networks, including Internet Service Providers (ISPs) and telecommunications networks. IS-IS supports traffic engineering capabilities, providing network administrators with the tools to control and optimize the flow of traffic across the network
9. Route Summarization:
Implement route summarization techniques to reduce the size of routing tables, especially in large-scale networks. This helps in optimizing routing efficiency.
10. Adaptability to Dynamic Network Changes:
Choose a routing protocol that can adapt to dynamic changes in the network, such as additions or removals of routers or links.
11. Support for IPv6:
If your network uses or plans to use IPv6, ensure that the chosen layer 3 routing protocol supports IPv6 seamlessly.
12. Training and Familiarity:
Consider the familiarity and expertise of your IT team with a particular routing protocol. Choosing a protocol your team is already skilled in can simplify configuration, troubleshooting, and maintenance.
By carefully considering these best practices, you can make informed decisions when selecting routing protocols and strategies that best suit your network's specific needs and goals.
CONCLUSION
Mastering Layer 3 routing is essential for building a solid network infrastructure and effective route traffic. Choosing the right routing protocol requires understanding network requirements, topology, and challenges.
Layer 3 routing best practices optimize network performance, reliability, and security. Network engineers must stay up-to-date with routing protocols and technology to adapt to the evolving network demands.
Ongoing engagement and collaboration within the community can drive the field forward. Continuous learning and peer review processes are encouraged to ensure network efficiency, security, and scalability. Together, we can face the future of networking with confidence.