You have no items in your shopping cart.

Palo Alto Firewalls: Complete Architecture & Features Guide
With cyber threats evolving unprecedentedly, traditional firewalls can no longer secure modern enterprise networks. Next-generation firewalls (NGFWs) have become the backbone of advanced network protection, and Palo Alto Networks is at the forefront of this innovation.
Palo Alto firewalls combine cutting-edge technologies, including App-ID for precise application control, Single Pass Parallel Processing (SP3) architecture for unparalleled performance, and WildFire threat intelligence for proactive threat detection.
By seamlessly integrating Zero Trust principles and cloud-native security, Palo Alto delivers robust protection for both legacy systems and hybrid cloud environments. As enterprises embrace hybrid infrastructures and face mounting cybersecurity challenges, understanding Palo Alto's NGFW architecture is critical for network security professionals.
This guide explains Palo Alto’s hardware architecture, advanced features, and enterprise-focused implementation strategies, equipping organizations for success in 2025 and beyond.
Core Concepts of Next-Generation Firewalls
Understanding the fundamental architecture of Next-Generation Firewalls (NGFWs) is crucial for appreciating Palo Alto's advanced capabilities. While traditional firewalls rely solely on basic filtering through IP addresses, ports, and protocols, NGFWs represent a paradigm shift in network security architecture, enabling more robust and adaptive protection.
What Sets NGFWs Apart?
NGFWs transcend conventional firewall limitations through four key technological innovations:
1. Application Awareness
NGFWs provide granular application control regardless of port, protocol, or IP address. This advanced traffic management capability enables security teams to identify and control specific applications, effectively blocking unauthorized access while maintaining business continuity.
2. User-Based Security Controls
Unlike traditional firewalls that focus solely on IP addresses, NGFWs implement identity-aware security policies. This evolution in access control allows organizations to enforce precise security measures based on user roles and responsibilities, significantly reducing insider threats and unauthorized access risks.
3. Comprehensive Threat Prevention
Modern NGFWs integrate multiple security functions:
- Intrusion Prevention Systems (IPS)
- Advanced antivirus protection
- Real-time malware detection
- Zero-day threat prevention
These integrated capabilities create a unified security framework that identifies and blocks both known and emerging threats before they can compromise network integrity.
4. SSL/TLS Traffic Inspection
As encrypted traffic becomes increasingly prevalent, NGFWs provide deep SSL/TLS inspection capabilities. This critical feature enables security teams to decrypt and analyze encrypted communications, uncovering potential threats hidden within seemingly secure connections.
Connecting to Palo Alto
Palo Alto Networks incorporates these core NGFW capabilities into its innovative SP3 architecture, App-ID technology, and WildFire threat intelligence, elevating NGFW performance to meet the demands of hybrid and cloud-native environments.
Key Features of Palo Alto Firewalls
Palo Alto Networks has revolutionized network security with cutting-edge features that set its firewalls apart as industry leaders. Each core technology is designed to address specific challenges while working seamlessly within the broader Next-Generation Firewall (NGFW) framework.
1. App-ID Technology: Behavioral Application Control
At the heart of Palo Alto's innovation is App-ID technology, which goes beyond traditional port-based identification to analyze application behavior patterns. This advanced capability enables firewalls to:
- Identify and control applications regardless of port, protocol, or encryption.
- Make real-time security decisions based on application behavior.
- Block evasive applications attempting to bypass security using non-standard ports.
- Leverage Applipedia Networks for a comprehensive database of application intelligence.
By enabling precise application control, App-ID ensures that businesses maintain productivity while minimizing security risks.
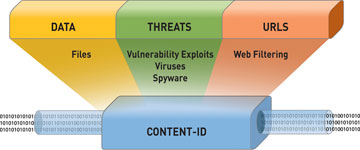
2. Content-ID: Advanced Threat Prevention
Content-ID acts as the firewall's deep inspection engine, delivering robust protection through:
- Real-time scanning for malware, viruses, and spyware.
- Dynamic web filtering to block harmful or inappropriate websites.
- Data filtering to prevent unauthorized transfers of sensitive information.
- Stream-based scanning for minimal latency and optimal performance.
This advanced threat prevention system ensures that threats are identified and neutralized before they can compromise the network.
3. User-ID: Identity-Based Security
Traditional IP-based security struggles to address the complexities of today’s mobile-first enterprise environments. User-ID overcomes these limitations by:
- Mapping network activity to user identities instead of static IP addresses.
- Enabling role-based security policies for precise access control.
- Providing detailed visibility into user activity across the network.
- Supporting comprehensive audit trails and forensic capabilities.
- Seamlessly integrating with enterprise authentication systems like Active Directory.
By linking user identities to network activity, User-ID enhances both security and visibility, aligning with Zero Trust principles.
4. GlobalProtect: Secure Remote Access
As remote and hybrid work becomes the norm, GlobalProtect extends enterprise-grade security to users beyond the corporate perimeter. Its capabilities include:
- Consistent enforcement of security policies for remote users.
- Seamless VPN connectivity across devices, ensuring secure access to enterprise resources.
- Integration with Zero Trust Network Access (ZTNA) principles for adaptive security.
- Real-time threat prevention to protect remote workers from evolving cyber threats.
- Automatic updates to security policies, ensuring ongoing protection.
GlobalProtect addresses the unique challenges of remote work environments, providing robust security without compromising user experience.
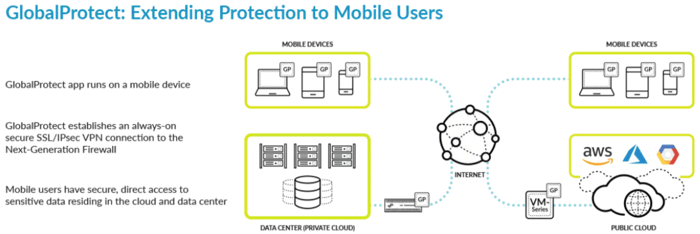
5. WildFire: Cloud-Based Threat Analysis
WildFire represents the future of proactive threat intelligence, leveraging the cloud for real-time protection. Its capabilities include:
- Advanced sandbox analysis to evaluate suspicious files and detect threats.
- Machine learning-powered detection of new and unknown malware.
- Real-time prevention of zero-day attacks, protecting networks from novel threats.
- Global threat intelligence sharing to enhance collective defense.
- Continuous adaptation to evolving attack techniques through AI-driven learning.
WildFire integrates seamlessly with Palo Alto’s SP3 architecture, ensuring rapid analysis and response to emerging threats.
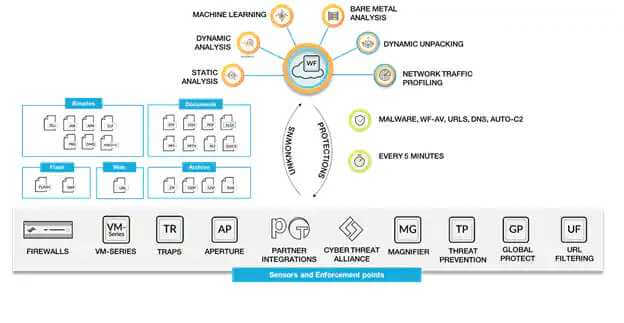
A Unified Security Framework
Each of these features builds upon the others, forming a comprehensive security ecosystem that adapts to modern threats while maintaining high performance. Powered by SP3 architecture, Palo Alto firewalls deliver unparalleled efficiency and scalability, ensuring that enterprises remain protected in an ever-evolving digital landscape.
The Evolution of Network Security with Palo Alto
As businesses shift to hybrid environments that combine on-premise data centers, public clouds, and branch offices, Palo Alto Networks has advanced its firewall technology to address these challenges.
Their firewalls seamlessly protect physical and virtual networks, utilizing Artificial Intelligence (AI) and Machine Learning (ML) to identify emerging threats quickly.
Palo Alto Networks also implements Zero Trust principles, meaning no device, user, or application is trusted by default, regardless of location. This model ensures continuous access verification, minimizing the risk of insider threats and lateral movement within the network.
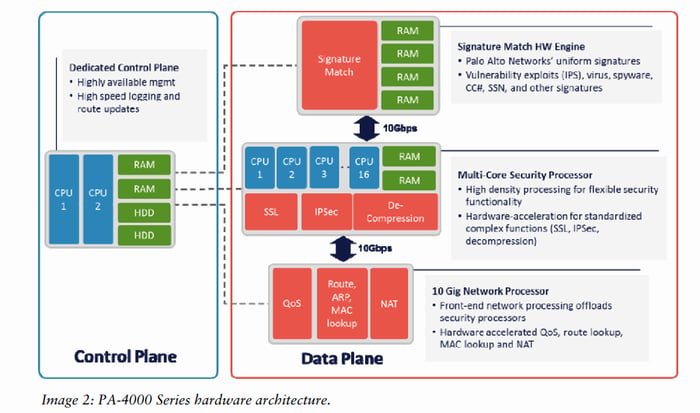
Hardware Architecture
The hardware architecture of Palo Alto Firewalls is designed to deliver high performance, scalability, and reliability while supporting advanced security features. Palo Alto Firewalls provide robust protection for modern network environments by combining purpose-built hardware components with intelligent software.
Purpose-Built Hardware
Palo Alto Firewalls utilize a proprietary hardware design optimized for efficient security processing without sacrificing performance. Key components of this architecture include:
1. Network Processing Units (NPUs):
- These are specialized chips responsible for handling high-speed data transfers and traffic forwarding.
- NPUs ensure low-latency performance, even under high bandwidth demands, by offloading packet-forwarding tasks from the main CPU.
2. Security Processing Units (SPUs):
- SPUs handle resource-intensive security functions such as malware scanning, SSL decryption, and intrusion prevention.
- This offloading improves performance by allowing the main CPU to focus on policy management and other non-intensive tasks.
3. Management Plane and Data Plane:
- The Management Plane is Dedicated to administrative tasks, configuration management, and logging. This separation ensures that operational tasks do not interfere with real-time traffic processing.
- The Data Plane is Designed for traffic inspection and enforcement of security policies. It ensures high-speed processing of network packets while applying security features.
We will be discussing this section in detail moving forward.
Single Pass Parallel Processing (SP3) Architecture
The hardware design is closely integrated with Palo Alto’s unique single-pass parallel Processing (SP3) Architecture, which provides high performance and efficiency in two ways:
a. Single Pass: Palo Alto Networks Firewall uses single-pass software to inspect each packet only once, enabling simultaneous content scanning, application identification, and policy enforcement.
This efficient design significantly reduces latency and computational overhead. The firewall handles various functions, including user identification (User-ID), policy lookup, traffic classification (App-ID), and threat detection through signature matching.
Processing packets in a single pass with a stream-based approach minimizes overhead and avoids the delays associated with separate scanning engines. This ensures high throughput and efficient threat blocking.
b. Parallel Processing: Palo Alto Networks’ parallel processing hardware ensures that function-specific tasks are executed simultaneously at the hardware level. Combined with the dedicated data plane and control plane, this design delivers exceptional performance.
By separating the data and control planes, Palo Alto Networks ensures each plane has dedicated hardware resources for specific tasks like application identification, threat prevention, and decryption.
This allows these processes to run concurrently, maintaining consistent performance even as security demands grow. Additionally, heavy utilization of one plane does not affect the platform's overall performance, ensuring reliability under high workloads.
Combining the Single-Pass approach with Parallel Processing allows Palo Alto Firewalls to inspect and secure traffic at high speeds without compromising protection. For more information, please refer to this link: https://www.paloguard.com/SP3-Architecture.asp
Palo Alto Firewall Control Plane & Data Plane:
Palo Alto Networks firewalls are designed with a clear separation between the Control and Data Planes, each serving a distinct purpose and optimizing the platform's performance.
1. Control Plane
The Control Plane manages the firewall's overall functionality and policy decisions. It handles high-level operations such as:
- Management of firewall policies: Defining and applying security policies, routing rules, and system configurations.
- Session management: Handling network session establishment, maintenance, and termination.
- Logging and reporting: Collecting and analyzing logs for monitoring, compliance, and troubleshooting.
- Threat intelligence updates: Receiving updates for antivirus signatures, URL filtering, and other threat intelligence feeds.
- Control traffic: Managing administrative tasks such as configuration changes and system health checks.
While the Control Plane is crucial for managing the system’s state and policies, it does not directly process network traffic.
2. Data Plane
The Data Plane is where the actual traffic processing happens. It handles network data flow and enforces the security policies set by the Control Plane. Key functions of the Data Plane include:
- Traffic inspection and filtering: Analyzing incoming and outgoing network traffic to ensure it complies with defined security policies.
- Application identification and control: Identifying and controlling applications running over the network, regardless of port or protocol.
- Threat prevention: Performing intrusion detection/prevention (IDS/IPS), antivirus, and malware analysis to block potential threats.
- Decryption: Handling SSL/TLS traffic decryption to inspect encrypted traffic for threats.
- Traffic forwarding: Forwarding legitimate traffic based on policy decisions made by the Control Plane.
The Data Plane is optimized for high throughput and low latency, ensuring efficient and secure traffic processing.
Separating the Control Plane and Data Plane in Palo Alto Networks firewalls enhances security and performance by dedicating resources to specific tasks. The Control Plane manages the policies and configurations, while the Data Plane ensures that high-performance traffic processing and security inspections are executed efficiently.
Note: Let me clarify that the hardware architecture of Palo Alto firewalls varies based on the models.
Reliability and Redundancy
Palo Alto Firewalls are engineered for maximum reliability, featuring:
- Redundant Power Supplies: Prevent downtime caused by power failures.
- Hot-Swappable Components: Enable quick replacement of parts without disrupting operations.
- Failover Support: Ensures uninterrupted service by automatically switching to a secondary device if the primary firewall fails.
These features are particularly critical for enterprise and data center environments, where uptime is essential.
Performance Metrics
The purpose-built hardware ensures scalability to meet the needs of diverse network environments, with support for:
- High Throughput: Handles multi-gigabit traffic without impacting performance.
- Concurrent Sessions: Supports millions of simultaneous sessions, ideal for large organizations with heavy traffic demands.
- High Availability: Maintains continuous operation with minimal latency, even during peak usage.
Palo Alto Firewalls’ hardware architecture exemplifies the balance between performance, security, and reliability. Its purpose-built design and the SP3 Architecture make it a leading choice for organizations seeking robust and efficient network security solutions.
Conclusion
Palo Alto Firewalls are at the forefront of modern network security, combining advanced hardware and software architectures to protect against cyber threats. Their specialized hardware features dedicated processing units and SP3 for minimal latency and maximum throughput in high-demand environments.
With capabilities such as application awareness, content inspection, user identification, and reliable redundancy, organizations can ensure strong security without compromising performance.
As businesses grow their digital infrastructures, Palo Alto Firewalls effectively safeguard critical network assets with exceptional precision and efficiency.
Disclaimer:
All images in this article are from the official Palo Alto Networks website and are used for illustrative purposes. Palo Alto Networks holds all rights to these images.
FAQs
1. What makes Palo Alto's SP3 architecture unique?
Palo Alto's Single Pass Parallel Processing (SP3) architecture performs all security functions in a single pass, significantly reducing latency while maintaining comprehensive protection. This efficient approach, combined with dedicated processing units, enables superior performance compared to traditional firewall architectures.
2. How does App-ID technology improve security?
App-ID provides granular application control by identifying applications based on their behavior rather than relying solely on ports, protocols, or encryption. This allows security teams to enforce precise policies, block unauthorized applications, and ensure better network visibility.
3. What are the key benefits of the dual-plane architecture?
Palo Alto's dual-plane architecture separates the Control Plane (handling management tasks) and the Data Plane (processing real-time traffic). This design ensures efficient resource allocation, consistent performance under heavy loads, and uninterrupted operations during administrative changes.
4. How does WildFire enhance threat prevention?
WildFire leverages cloud-based sandboxing and machine learning to detect and prevent zero-day threats. Analyzing suspicious files in real-time provides proactive protection against emerging malware and shares intelligence globally to strengthen collective defenses.
5. Can Palo Alto firewalls handle encrypted traffic?
Yes, Palo Alto firewalls are equipped with SSL/TLS traffic decryption capabilities, allowing them to inspect encrypted communications for potential threats. This ensures comprehensive protection without compromising performance or security.