You have no items in your shopping cart.

DPI in IPv6 Era: Advanced SSL/TLS Techniques on Fortinet Firewalls
This article covers the role of Deep Packet Inspection (DPI) in network security in the IPv6 era, with a focus on SSL/TLS techniques implemented by Fortinet Firewalls. It discusses DPI fundamentals, IPv6-specific applications, and strategies for ensuring network safety.
In the modern landscape of network security, Deep Packet Inspection has emerged as a crucial tool, especially in the IPv6 era, which is the latest advancement in Internet Protocol.
In this discussion, we explore the importance of advanced SSL/TLS techniques on Fortinet Firewalls. Deep Packet Inspection is crucial for managing computer networks. It detects anomalies and protects against unknown attacks by inspecting and analyzing network traffic, making it an essential tool for network administrators.
The discussion includes the implications for Internet service providers, network operators, and the broader Internet society. We underline that Deep Packet Inspection is crucial for securing networks and data across different devices, including mobile phones.
DPI Fundamentals
Deep Packet Inspection is a network security mechanism that goes beyond the basic examination of packet headers. DPI analyses the data part of network packets to monitor and filter content, ensuring higher levels of security. This technique is essential in identifying, classifying, and stopping threats that standard detection methods might miss.
DPI provides a detailed view of the data flow by analyzing the entirety of data packets, allowing for more precise control over data flow. Contemporary cybersecurity strategies rely heavily on it to prevent data breaches and enforce network policies. This is particularly true for complex network environments that use Internet Protocol Version 6 (IPv6).
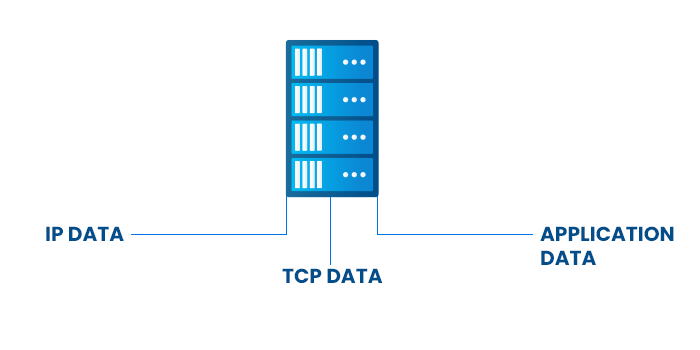
Deep Packet Inspection is a type of packet filtering that looks for protocol non-compliance, viruses, spam, intrusions, or specified criteria in the data portion of a packet as it passes an inspection point. Based on these findings, the system determines whether the packet can pass or must be quarantined.
Whereas traditional methods only examine IP/TCP data, DPI goes a step further to inspect the Application portion as well. This provides a more comprehensive solution to address the introduction of unwanted or malware-infected data into desired data. This process enables network administrators to understand, control, and manage network data flow more effectively.
Advanced Deep Packet Inspection technologies are used by Fortinet firewalls to improve network safety. Remember that features and methods can change over time, so it's important to consult the most recent documentation offered by Fortinet to ensure you have the most recent and accurate information.
Capabilities of DPI
The following are the key characteristics of Deep packet inspection:
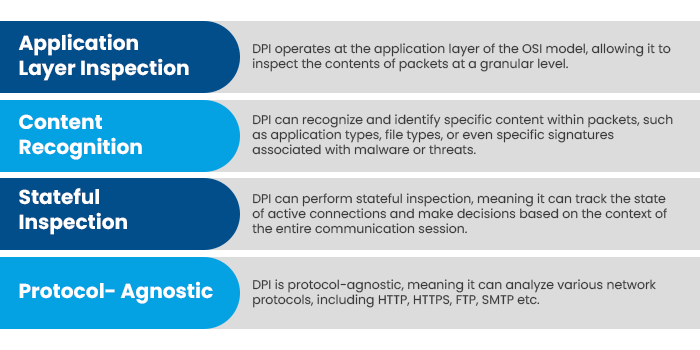
Why DPI?
While the need for DPI solutions is clear, implementing them comes with challenges. DPI can be resource-intensive, requiring powerful hardware to inspect large amounts of data flow in real-time. Security teams must also stay up-to-date on the latest hazards to configure their DPI systems to detect them.
Organizations should start by implementing DPI on their Internet connections first, where external threats are more likely to originate. Over time, they can expand DPI coverage to their entire network as well. Some of the key areas of focus are:
-
Inspecting incoming and outgoing data flow for known malware and attacks
-
Blocking unauthorized IPv6 traffic until a full security review can be performed
-
Monitoring for signs of IPv6-based denial of service attacks
-
Scanning files transferred over the network for suspicious content
DPI solutions can provide valuable insight into network activity and threats. With the proper implementation and ongoing management, they can help businesses detect and mitigate risks posed by the rise of IPv6 and tunneling. Security teams should work with their DPI vendors to create an implementation plan that balances effectiveness, performance, and manageability.
In summary, while transitioning to IPv6 is inevitable, DPI can help secure organizations during this transition period and beyond. A phased approach, starting with high-risk areas and expanding over time, is recommended. With the proper controls, DPI solutions can help maintain network safety as networks evolve.
DPI's Impact on Network Traffic in the IPV6 Era
Analyzing the content of IPv6 packets at the application layer allows for insights into traffic nature, security policy enforcement, and network performance optimization. The techniques for DPI on IPv6 traffic are similar to those for IPv4 (Internet Protocol Version 4) but are tailored to the unique characteristics of the IPv6 protocol.
The transition to IPv6 has significant impacts on network management and security, affecting both individual users and large businesses. As internet service providers (ISPs) increasingly adopt IPv6, DPIs play a crucial role in managing and securing these new network architectures.
Here's a summary of the application of DPI to IPv6 traffic:
Internet Protocol Analysis: IPv6 Header Inspection
DPI devices analyze the IPv6 header to retrieve details like source and destination addresses, traffic class, flow label, and the next header field, offering fundamental information about the packet and its intended destination.
Analyzing Next Header
The Next Header field in the IPv6 header is inspected to establish the next header type in the packet. DPI devices utilize this data to recognize the payload type, allowing them to handle the following headers and protocol-specific details.
Extension Header Processing
IPv6 offers extension headers that supply extra details for particular protocols. DPI devices examine and handle these extension headers to comprehend the encapsulated protocols, including Fragmentation, Authentication, and Hop-by-Hop options.
Transport Layer Protocol Inspection
DPI analyzes the payload of IPv6 packets at the transport layer to identify the specific transport protocols being used, such as TCP, UDP, or ICMPv6. This allows DPI devices to understand the nature of the traffic.
SSL/TLS Inspection
DPI methods are used to inspect IPv6 traffic for SSL/TLS. This includes decrypting SSL/TLS-encrypted packets, examining the payload for potential threats, and re-encrypting the data flow. This process enables the detection of malicious activities within encrypted connections.
Application Layer Inspection
DPI devices analyze the application layer of IPv6 traffic to detect particular applications, services, or protocols. This detailed visibility enables the implementation of conservative policies based on the type of applications in use.
Content Filtering
DPI is employed to filter content on IPv6 to manage access to websites and applications according to categories. This involves examining the content of IPv6 packets and implementing policies to either permit or prohibit specific content.
There are many other applications of DPI on IPV6 traffic beyond the ones listed.
DPI USE CASE EXAMPLES
Deep packet inspection can also be used for a variety of security applications and threat detection. Some examples include:
-
Deep Content Inspection in SSL/TLS
-
Malware Detection
-
Intrusion Detection
-
Forensics and Incident Response
-
Data Loss Prevention
Advanced SSL/TLS techniques on Fortinet Firewalls
To ensure that malicious activity is identified and neutralized even within encrypted connections, Fortinet firewalls employ deep packet inspection techniques to examine and analyze the content of SSL/TLS-encrypted data. After decrypting SSL/TLS-encrypted packets and examining the payload, the communication is re-encrypted for safe transmission.
Fortinet Firewalls use specialized techniques to handle SSL/TLS traffic over IPv6. They efficiently manage IPv6's complex header structure, leverage its security features, and maintain network performance despite larger packet sizes. These firewalls are also scalable, ensuring effective and reliable SSL/TLS inspection as networks evolve and IPv6 becomes more widespread.
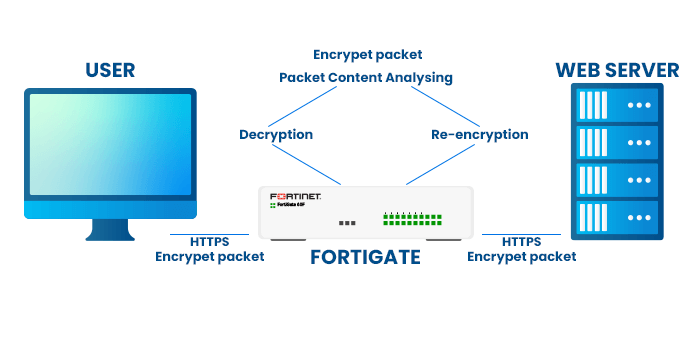
The following are thorough descriptions of the SSL/TLS deep packet inspection techniques used on Fortinet firewalls:
1. Signature-based detection:
Fortinet firewalls utilize signature databases to detect known threats, such as viruses, malware, and other malicious activities. Keeping these databases updated is essential for staying protected against the latest threats.
2. Behavioral analysis:
Behavioral analysis may be used by Fortinet firewalls to identify abnormal patterns or behaviors that could indicate an attack. This involves monitoring network activity for deviations from normal baselines.
3. Heuristic analysis:
Heuristic analysis involves identifying potentially malicious code by examining its behavior and characteristics instead of relying on known signatures. Fortinet firewalls may use heuristic technologies to detect new, previously unseen risks.
4. Application Control:
Fortinet firewalls have the capability to identify and control the use of specific applications within the network. This includes the ability to allow or block certain applications based on policies defined by administrators.
5. SSL Inspection:
Fortinet firewalls can conduct SSL inspection to decrypt and inspect encrypted traffic for potential threats before re-encrypting and forwarding it.
6. Intrusion Prevention System:
Intrusion Prevention System (IPS) modules in Fortinet firewalls monitor and analyze network and/or system activities for malicious exploits or security policy violations. They can then act to prevent the detected threats.
7. Anomaly Detection:
Anomaly detection techniques may be used by Fortinet firewalls to identify deviations from normal network behavior. Unusual patterns or spikes in data flow may trigger alerts or actions to mitigate potential safety issues.
8. Content Filtering:
Fortinet firewalls can enforce content filtering policies to control access to websites based on categories, helping to prevent users from accessing malicious or inappropriate content.
9. Zero-Days Protection:
To protect against zero-day threats, Fortinet firewalls use advanced techniques such as sandboxing, which involves executing suspicious code in an isolated environment to observe its behavior and detect potential threats.
10. Customs Signature:
The deployment of custom signatures by administrators in Fortinet firewalls enhances the detection of specific threats.
Technical Steps involves in DPI methods on Fortinet Firewalls:
· SSL Inspection:
Fortinet firewalls conduct SSL inspection by decrypting SSL/TLS-encrypted traffic for thorough payload examination. Following inspection, the traffic is re-encrypted before being forwarded to its destination.
· Man-in-the-Middle Decryption:
Fortinet firewalls function as a trusted intermediary between the client and server during the SSL/TLS handshake, allowing the firewall to decrypt and inspect the traffic. This deployment strategy prevents attackers from utilizing encryption to conceal malicious activities.
· Certificate Authority (CA) Certificate Deployment:
The deployment of a CA certificate in Fortinet firewalls is critical to producing certificates for SSL/TLS sessions. Clients within the network trust the firewall's CA certificate, permitting the firewall to decrypt and inspect traffic without triggering certificate warnings on client devices.
· Certificate Chain Verification:
Fortinet firewalls validate the complete certificate chain during SSL/TLS handshakes to ensure the authenticity of the certificates used in the connection. This entails checking the certificate's digital signature and confirming the chain up to a trusted root certificate.
· Certificate Revocation List (CRL) and Online Certificate Status Protocol (OCSP) Checking:
The deployment of CRL and OCSP checking mechanisms in Fortinet firewalls is a crucial step to ensure certificate validity. This guarantees that certificates used in encrypted connections have not been revoked, adding an additional layer of protection.
· Forward Secrecy (FS) Support:
Fortinet firewalls support Forward Secrecy, which enhances the security of SSL/TLS connections by generating unique session keys for each session. Even if a private key is compromised, past communications remain secure.
· Protocol and Cipher Suite Inspection:
Fortinet firewalls inspect the SSL/TLS handshake to ensure that only secure protocol versions and cipher suites are used. This includes the capability to block deprecated and vulnerable versions of SSL/TLS.
· Content Filtering and Threat Detection:
Once decrypted, the content of SSL/TLS-encrypted traffic is subject to content filtering and threat detection mechanisms. Fortinet firewalls can analyze the payload for malware, viruses, and other threats.
· Application Control:
Fortinet firewalls enforce application control policies even within SSL/TLS-encrypted traffic. This helps prevent the unauthorized use of applications and services that may pose safety risks.
· SSL/TLS Profile Configuration:
Administrators can create and configure SSL/TLS profiles to define specific security policies. These profiles allow for fine-tuning of SSL/TLS settings, including ciphers, protocols, and certificate requirements.
· SSL Session Information Logging:
Fortinet firewalls offer visibility into SSL/TLS sessions, logging information such as source and destination, protocols used, and other pertinent details.
Additionally, always refer to the latest Fortinet documentation for the most accurate and up-to-date information on SSL/TLS deep packet inspection techniques.
General guidelines for SSL/TLS on Fortinet firewall:
1. Accessing Fortinet :
While the firewall can be accessed via two methods CLI, i.e. SSH and Web, here the method followed is Web access so:
(For reference: The firewall model is Fortigate 1801F, and OS is FortiOS 7.4.2)
To access the Fortinet Firewall, open a web browser and enter the device's IP address in the address bar. Then, log in using the appropriate credentials.
2. Navigate to SSL Settings:
To find the SSL/TLS inspection settings, navigate to the corresponding section within the firewall's management interface, usually located in the security or policy configuration area. Once there, implement SSL inspection by activating the global SSL inspection feature or adjusting SSL inspection settings within specific security policies.
3. Certificate Authority Setup:
If necessary, import the Certificate Authority (CA) certificate to generate SSL/TLS session certificates, ensuring that client devices do not encounter certificate warnings.
4. Configuring Encryption cipher suites:
Next, configure the allowed cipher suites and SSL/TLS protocols, opting for secure options while avoiding outdated and vulnerable choices. Adjust the settings for certificate chain verification, including checking Certificate Revocation Lists (CRLs) and using the Online Certificate Status Protocol (OCSP) if needed. If supported, configure application control and threat detection for SSL/TLS-encrypted traffic to bolster protection.
5. SSL/TLS Profile:
Create and customize SSL/TLS profiles to establish specific security policies aligned with your organization's needs. Finally, explore monitoring and logging options to analyze SSL/TLS session information and address potential safety concerns.
Conclusion
Equipped with all the arsenal to face cybersecurity challenges, Fortinet is undoubtedly one of the top-notch firewalls to introduce into one’s premises.
Keep in mind that these steps serve as general guidelines, and the specific steps may differ based on the Fortinet firewall model and firmware version you have. It is always advisable to refer to the official documentation for precise configuration instructions tailored to your device.
To check the detailed specifications of your device, CLICK HERE.