You have no items in your shopping cart.
Network Devices Blog
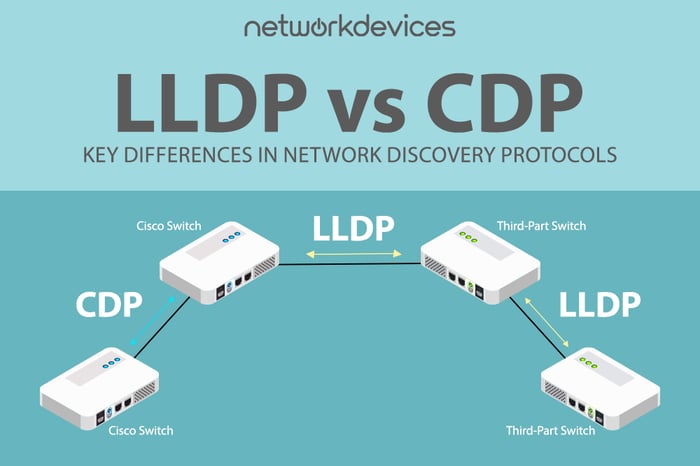
LLDP vs. CDP: Key Differences in Network Discovery Protocols
Comparison | Software/License/Protocol
Navigating a complex network is like navigating a sprawling city without a GPS. Each device and connection can seem like an unknown node, making it challenging to understand or document the network...

CrowdStrike Crash Causes Windows BSOD Errors Worldwide
Software/License/Protocol | News
The global cybersecurity leader CrowdStrike has been reported to experience a significant issue, leading to a global Windows system outage. This has severely impacted major sectors including finance,...
Common Security Risks Associated with Firewall Pinholes
Software/License/Protocol | Firewall
Have you ever had uninvited guests snooping around on your data? Just like leaving a door unlocked, leaving firewall pinholes open can invite digital drama. A firewall pinhole is an open port that permits...
UniFi G5 PTZ: Discreet Business Security
News
The UniFi G5 PTZ sets a new standard for business security with its compact and versatile design, featuring 2K (4MP) video resolution for high-quality video capabilities. This all-weather camera is...
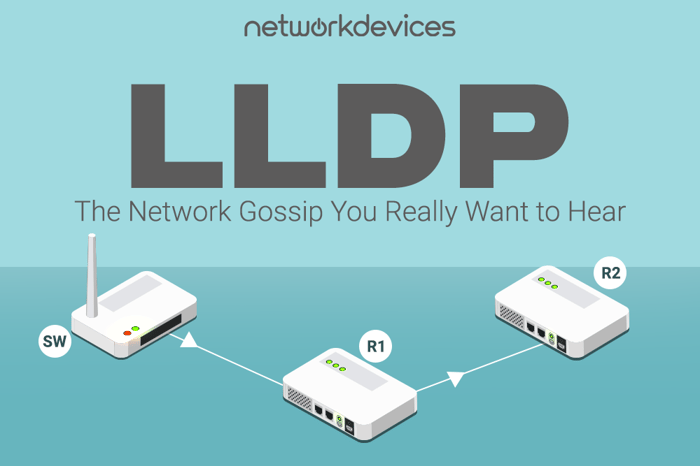
LLDP: The Network Gossip You Really Want to Hear
Software/License/Protocol
LLDP, or Link Layer Discovery Protocol, is an essential tool in the evolving threat landscape of network management. Recent cyber-attacks, like the SolarWinds breach and the Colonial Pipeline ransomware...
CRS320-8P-8B-4S+RM Is Here: The first POE++ MikroTik Switch
News | MikroTik
Is your network tangled in cables and outdated tech? The MikroTik CRS320-8P-8B-4S+RM is here to streamline your infrastructure with unmatched power and efficiency. This isn’t just another switch...
NDR vs. EDR vs. XDR vs. MDR: Detection & Response in Cyber Security
Comparison | Software/License/Protocol
In this comprehensive guide, we'll delve into the differences between NDR vs. EDR vs. XDR vs. MDR, helping you understand which threat detection and response platform is best suited to protect your...

AXIS W102: Revolutionize Evidence Collection
News
In an era where security and accountability are paramount, and challenges like low-quality footage and data security concerns plague evidence collection, AXIS Communications has set a new benchmark with...
Firewall Types Unmasked: The Passport to a Safer Network
Firewall
A firewall is a security device that controls the inbound and outbound traffic through security policies. Traditionally, firewalls are used to allow network traffic based on source and destination IP...
XDR: The Future of Cybersecurity, Now
Software/License/Protocol
As cyber threats evolve, so must our defense strategies. Extended Detection and Response (XDR) represents the next step in cybersecurity, promising a unified and proactive approach to threat detection...





